Back to Blog 


DeFiAudit
Security Alpha: Transform Your Smart Contracts into Liquidity Magnets
In the early days of DeFi, TVL was a function of greed. High APYs, fueled by aggressive token emissions, acted as a magnet for "mercenary capital"—liquidity that arrives with the first yield farm and vanishes at the first sign of a better deal or a minor exploit.
As the ecosystem matures toward a $60 billion+ global infrastructure, the nature of capital is changing. Sophisticated LPs and institutional players no longer look at nominal yield; they look at risk-adjusted returns. In this environment, security is no longer a cost center or a defensive checkbox. It is an offensive weapon. It is the "Alpha" that allows a protocol to maintain "sticky liquidity" even when competitors offer higher rewards.
If you are building the next generation of DeFi, your primary product isn't your swap engine or your lending pool—it's your Trust Architecture.
The hard way: building a fortress protocol from scratch

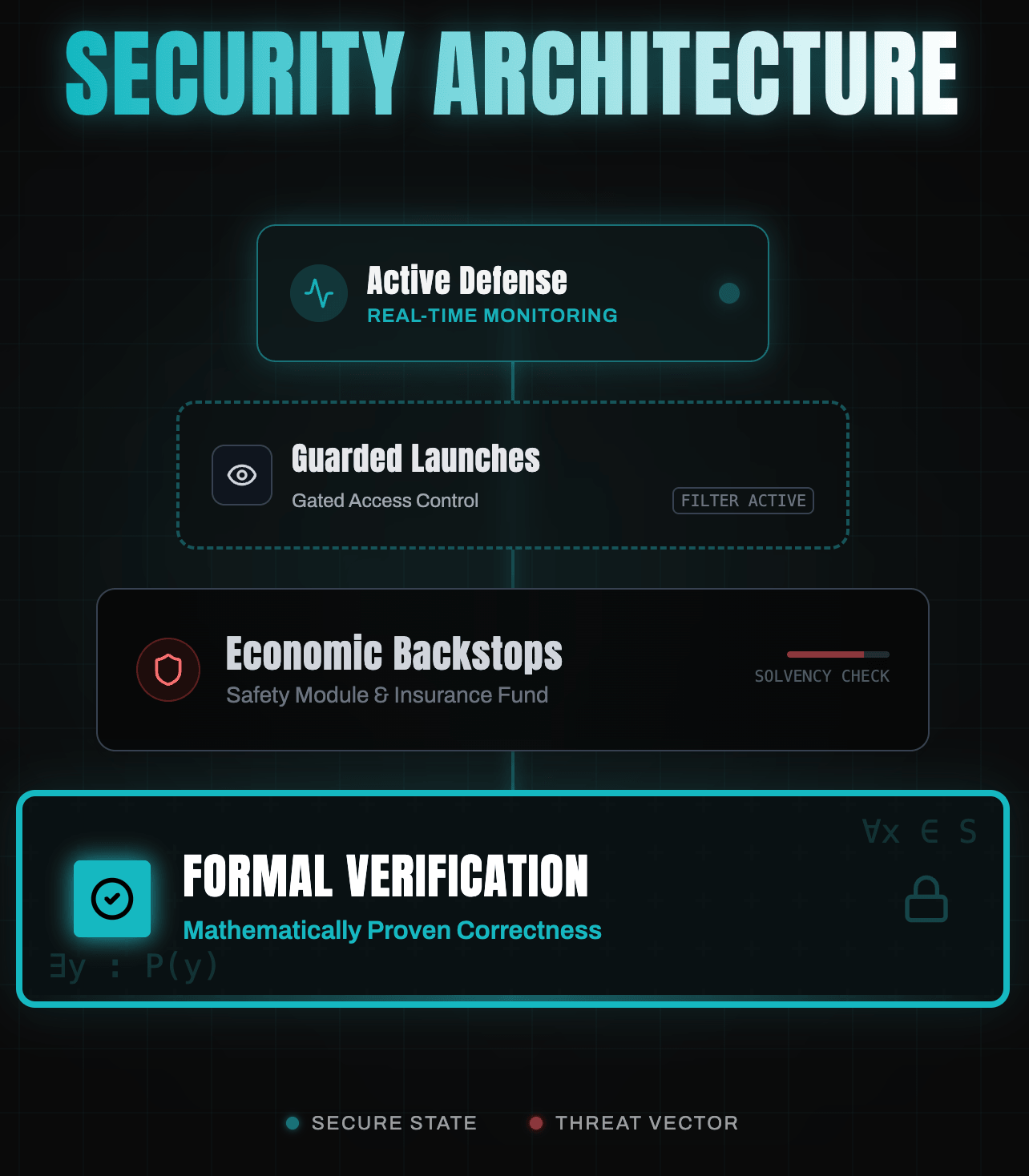
To understand why security correlates with TVL, we must look at the immense technical burden of building a protocol that can safely hold $1B+. If you were to build this "the hard way," without shortcuts, here is the blueprint you would have to follow.
1. Moving beyond unit tests: formal verification
Simple test suites are insufficient for complex logic like concentrated liquidity or recursive lending. To attract deep liquidity, you must prove the mathematical correctness of your code.

The challenge: You must define "invariants"—properties that must always remain true (e.g., "the total debt can never exceed total collateral").
The manual path: This requires using symbolic execution tools and formal verification languages (like Coq or the K-Framework). You are essentially writing a mathematical proof for every function in your smart contract. Most developers skip this because it adds months to the development cycle, but it's why protocols like Uniswap v3 have remained unexploited despite their complexity.
2. Engineering economic backstops (the safety module)
Code security isn't enough; you must prepare for "Black Swan" economic events.
The challenge: If a liquidation fails due to network congestion or an oracle lag, the protocol becomes insolvent.
The manual path: You must build an on-chain "insurance" layer. This involves creating a staking module where users deposit the protocol's native token (or an LP token) to act as a backstop. In the event of a "shortfall," the protocol must be programmed to automatically "slash" these staked assets to recapitalize the system. Managing the incentives for these stakers while ensuring the slashing logic is airtight is a massive engineering undertaking, similar to Aave's Safety Module.
3. Implementing guarded launches (the "psychological scarcity" logic)
Launching wide-open is a liability. The most successful protocols today use "Guarded Launches."
The challenge: You need to build dynamic, adjustable caps into your contracts.
The manual path: You must engineer a system of global and per-user deposit limits that can be increased via governance. This requires a robust administrative layer and a "Timelock" (typically 48-72 hours) to ensure that if a cap is raised maliciously, users have time to exit.
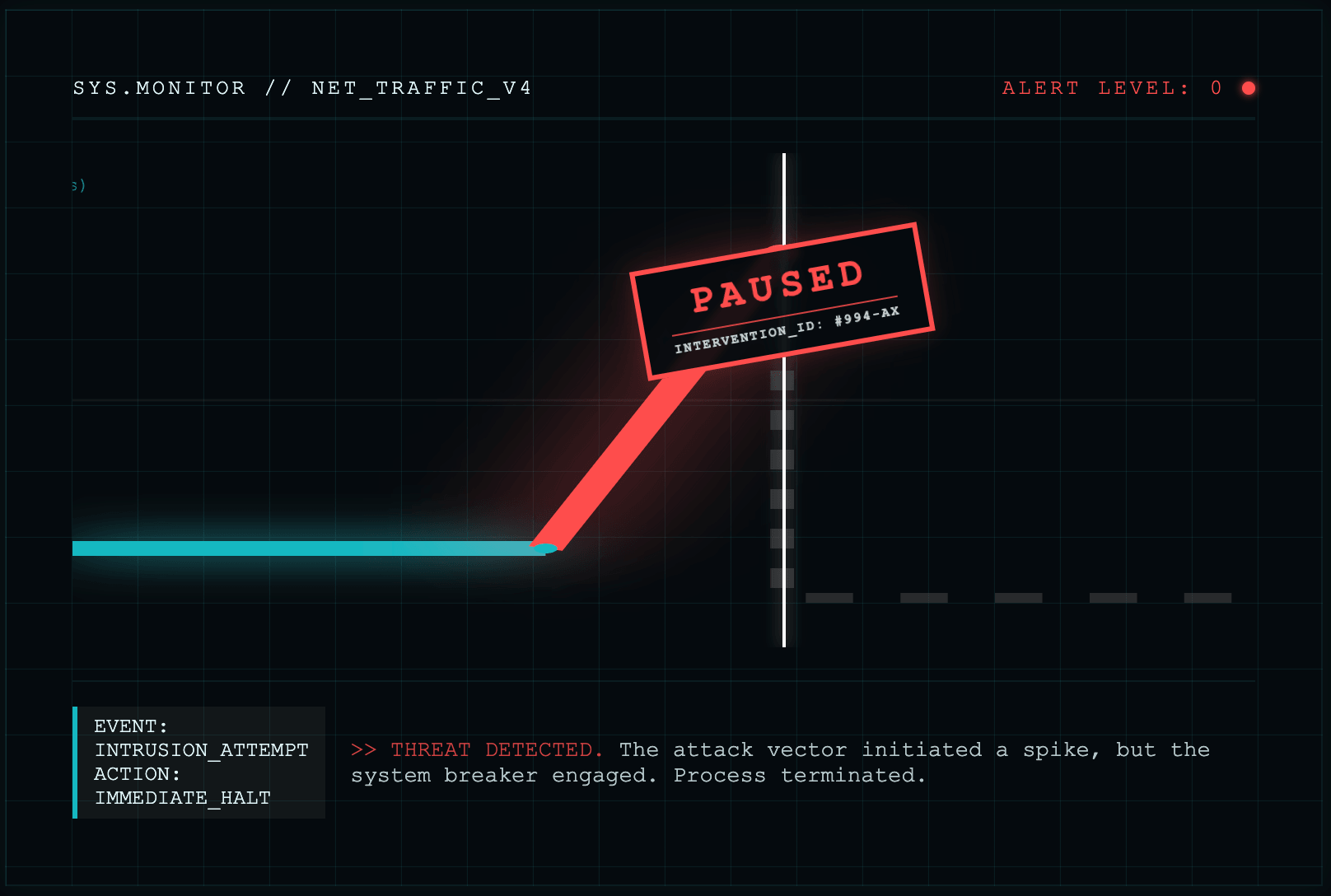
4. Active defense: circuit breakers and risk monitors
Static code is a sitting duck. High-TVL protocols require active, real-time defense.

The challenge: How do you stop a $200M exploit while it’s happening?
The manual path: You must implement "Circuit Breakers"—automated logic that pauses deposits or withdrawals if an outflow exceeds a certain velocity (e.g., 20% of TVL leaving in 10 minutes). You also need to build or integrate an "Antifraud Network" that monitors transactions in the mempool or immediately after execution to detect anomalies before they cascade.
Best practices: the "why" behind architectural decisions
When you choose to implement these features, you aren't just "securing code"; you are making economic decisions that influence your TVL trajectory.
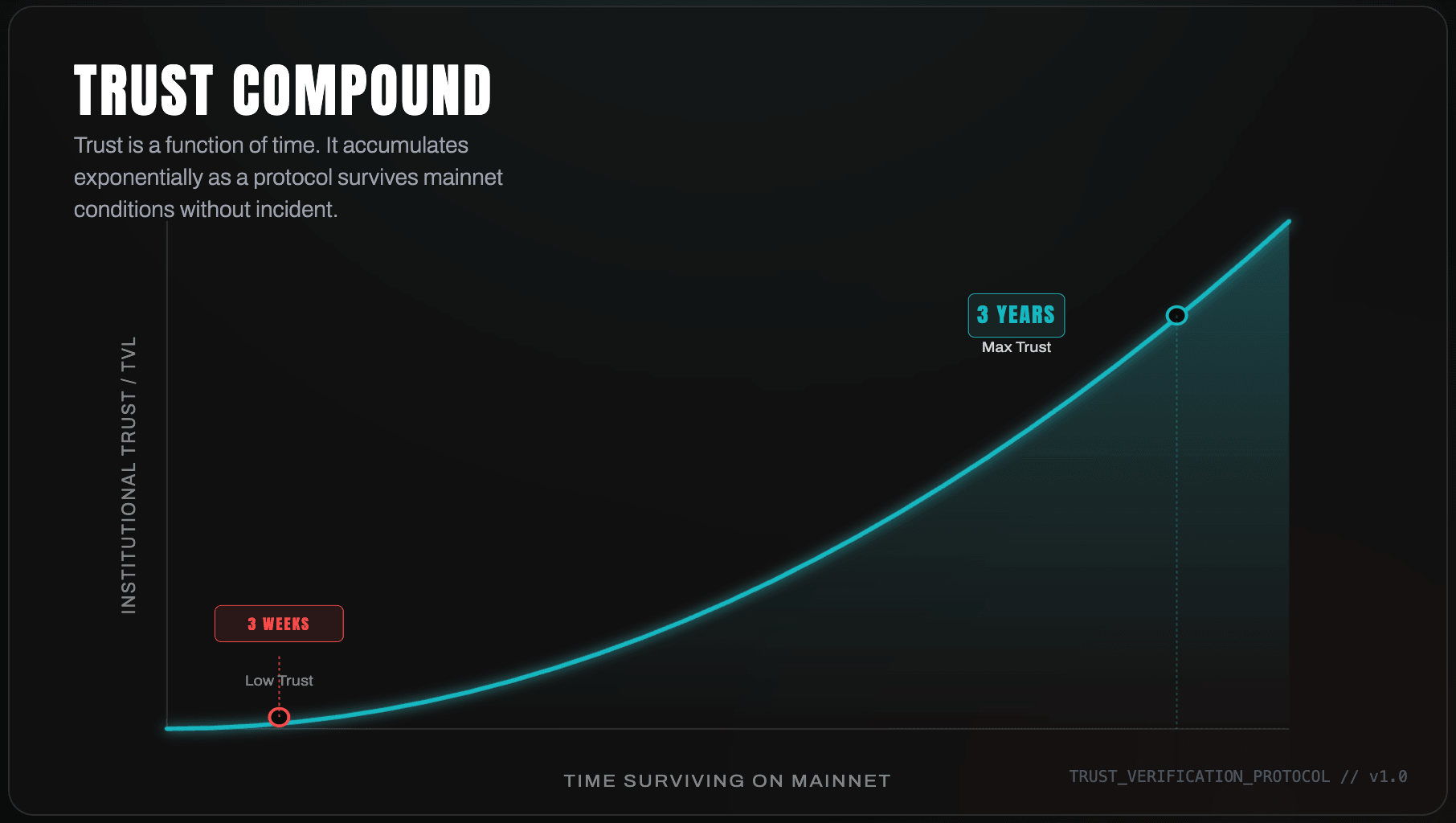
The Lindy effect as a moat
In DeFi, the longer a protocol survives with a high TVL, the more likely it is to survive in the future. This is the Lindy Effect. By prioritizing immutability (like Uniswap) or rigorous governance (like MakerDAO), you are building a "track record" that acts as a barrier to entry for new forks. Institutions will always choose a 5% yield on a "Lindy" protocol over a 15% yield on a three-week-old fork.

The "whitehat" economy
A robust Bug Bounty program (via platforms like Immunefi) is effectively a disaster insurance policy.
Best practice: Scale your bounty to the "Primacy of Impact." If your TVL is 5k bounty is an insult—and an incentive for a hacker to go blackhat. A $1M+ bounty, combined with a "Safe Harbor" agreement, aligns the hacker’s rational economic interest with the protocol’s survival.
Isolated risk vs. shared risk
Protocols like Morpho Blue are proving that Risk Isolation is a major driver of TVL.
Why: In shared-pool models (like Aave), one "toxic" asset can threaten the entire pool. By building isolated markets, you allow LPs to choose their specific risk appetite. This granularity attracts "Smart Capital" that avoids the systemic contagion risks of older DeFi models.
The institutional gatekeepers
To reach the next trillion in TVL, your protocol must pass the "Institutional Filter." This isn't about marketing; it's about compatibility with the tools institutions use.

Custody compatibility: If your protocol doesn't support MPC (Multi-Party Computation) or isn't "whitelisted" by platforms like Fireblocks, you are invisible to 90% of institutional capital.
Verifiable TVL (vTVL): Sophisticated analysts are moving away from "Gross TVL" (which can be faked with recursive looping) to "Verifiable TVL." If your architecture is opaque or relies on centralized oracles, you will fail the due diligence of any serious fund.
Conclusion
The correlation is clear: Security is the primary product; yield is just the incentive.
Building a protocol that can withstand the "Dark Forest" of Ethereum requires more than just clever Solidity. It requires a multi-layered architecture of formal verification, economic backstops, and active monitoring.
While it is possible to build these layers manually from scratch, the complexity and time-to-market often become prohibitive. This is where specialized security frameworks and automated audit tools become essential. They don't just "find bugs"—they provide the infrastructure that allows you to prove your protocol's integrity to the world, turning security into your greatest engine for TVL growth.
If you want to win the liquidity war, stop fighting over APY and start building for resilience. In the long run, the capital always flows to where it is safest.
Get in touch
At Zealynx, we specialize in the advanced security architectures and formal verification techniques discussed in this article. Whether you are building a high-TVL protocol, auditing a complex DeFi system, or need expert guidance on economic risk and guarded launches, our team is ready to assist — reach out.
Want to stay ahead with more in-depth analyses like this? Subscribe to our newsletter and ensure you don’t miss out on future insights.
FAQ: Security as a Growth Engine
1. How does security directly impact a protocol's TVL?
Security has shifted from a defensive necessity to a primary driver of liquidity (TVL). Institutional investors and sophisticated LPs prioritize "risk-adjusted returns" over raw APY. A protocol with a robust Trust Architecture—proven through formal verification and economic backstops—attracts "sticky liquidity" that stays for the long term, whereas insecure protocols only attract mercenary capital that flees at the first sign of risk.
2. What is the difference between a standard audit and formal verification?
A standard audit is a manual review where experts look for bugs and logic errors, which is essential but cannot guarantee 100% security. Formal Verification goes a step further by creating a mathematical proof that the code behaves exactly as intended under all possible states. It allows you to prove "invariants" (e.g., "users can always withdraw their collateral") are mathematically impossible to break.
3. What is a "Guarded Launch" and why is it necessary?
A Guarded Launch is a strategy where a protocol launches with strict limits on deposit amounts (TVL caps) which are gradually raised over time. This creates "psychological scarcity" that drives demand while limiting the "blast radius" of any potential early bugs. It prevents a scenario where a protocol loses hundreds of millions in an exploit on Day 1.
4. Why is the "Lindy Effect" critical for institutional adoption?
The Lindy Effect posits that the longer a technology survives, the longer it is likely to survive in the future. In DeFi, time without an exploit is the ultimate metric of security. Institutions are far more likely to trust a protocol that has survived 3+ years on mainnet (like Uniswap or MakerDAO) than a new fork, even if the new fork offers higher yields. Building this track record requires prioritizing immutability and conservative governance.
Glossary
| Term | Definition |
|---|---|
| Chainlink | Leading decentralized oracle network providing secure data feeds for DeFi. |
| Price Manipulation | Attacks artificially moving asset prices to exploit dependent protocols. |
| Proof of Reserve | Cryptographic verification that reserves back on-chain token supply. |
| Transaction | Signed message that changes blockchain state, requiring gas payment. |
| Ownable | Access control pattern providing single-address ownership for admin functions. |
| Modifier | Reusable Solidity code blocks for access control and input validation. |