Back to Blog 


SolanaSecurity ChecklistWeb3 Security
Solana Smart Contract Audit Guide 2026: Firedancer, Token-2022 & Security Checklist
The monolithic, high-speed experimental phase of Solana has concluded. In 2026, the transition to a multi-client environment, driven by the Firedancer validator and the ubiquity of Token-2022 (Token Extensions), has rendered legacy auditing frameworks obsolete. Security is no longer a localized evaluation of Rust logic; it is now a multi-dimensional problem spanning hardware-driven consensus lag, programmable asset transfer hooks, and localized economic contention. If your security model hasn't shifted from "syntax-first" to "systemic-resilience," your protocol is effectively unverified.
The Hardware Arms Race: Firedancer and the "Skip-Vote" Vulnerability
The dominance of the Firedancer client has moved the network's performance limit to the hardware layer. With the activation of SIMD-0370, rigid Compute Unit (CU) caps have been replaced by dynamic block sizing. This introduces two critical risks for protocol architects:
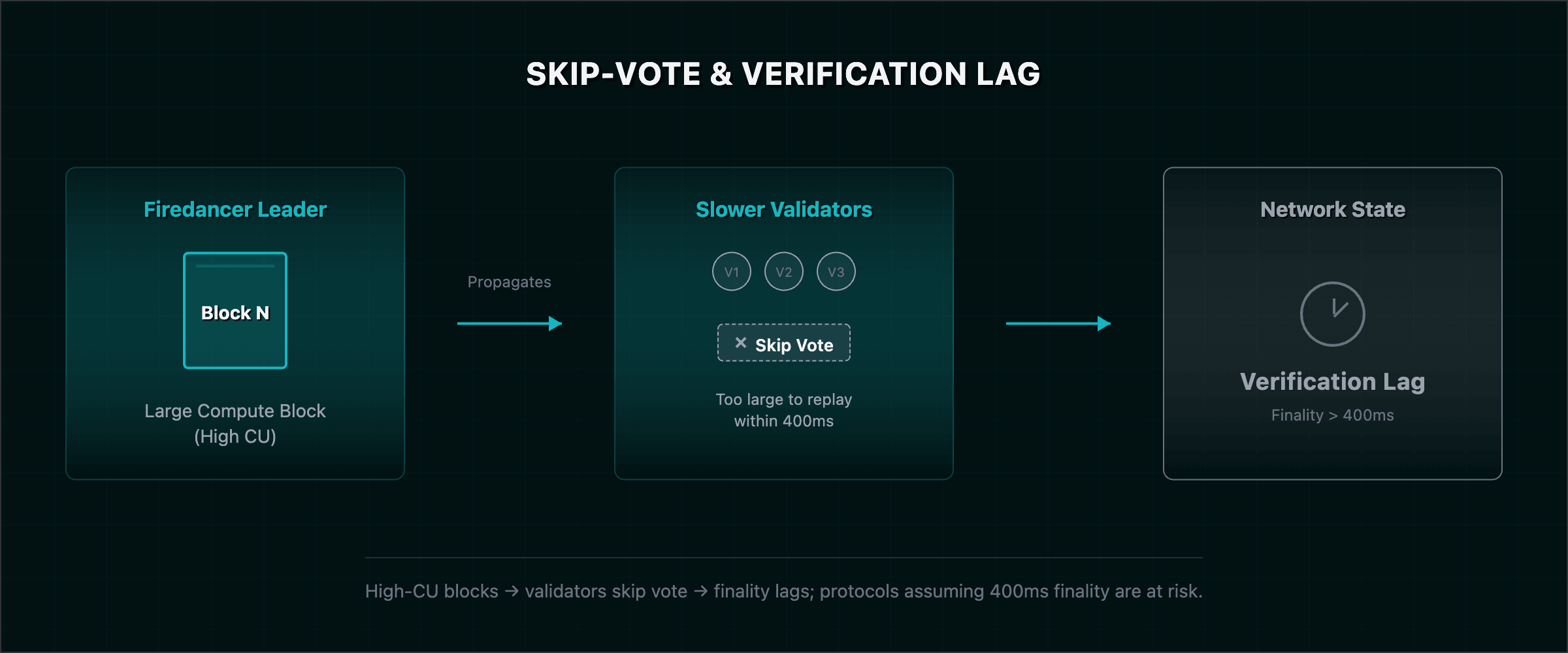
- The Skip-Vote Phenomenon: Under the Alpenglow consensus model, high-performance leaders can produce blocks containing hundreds of millions of CUs. While Firedancer handles this, weaker validators (running older hardware or the Agave client) may fail to process these blocks within the 400ms slot time. These validators will "skip" voting rather than halt.
- The Danger: If your protocol relies on 400ms finality for liquidations or oracle updates, you are now exposed to "Verification Lag." A transaction included by a high-performance leader might suffer from delayed finality as the rest of the network catches up, creating a window for micro-reorgs or bridge-latency exploits.

Audit Requirement: Inspect all time-sensitive instructions for
valid-until-slot checks and explicit slippage tolerances that account for slot-based timing variance. Understanding how audit costs scale in 2026 helps budget for Solana-specific review depth.Token-2022: The Return of Reentrancy via Transfer Hooks
Token-2022 (Token Extensions) have introduced complexity that mirrors Ethereum's historical pitfalls. The Transfer Hook extension, while powerful, reintroduces control-flow risks that were previously absent in the Solana account model.
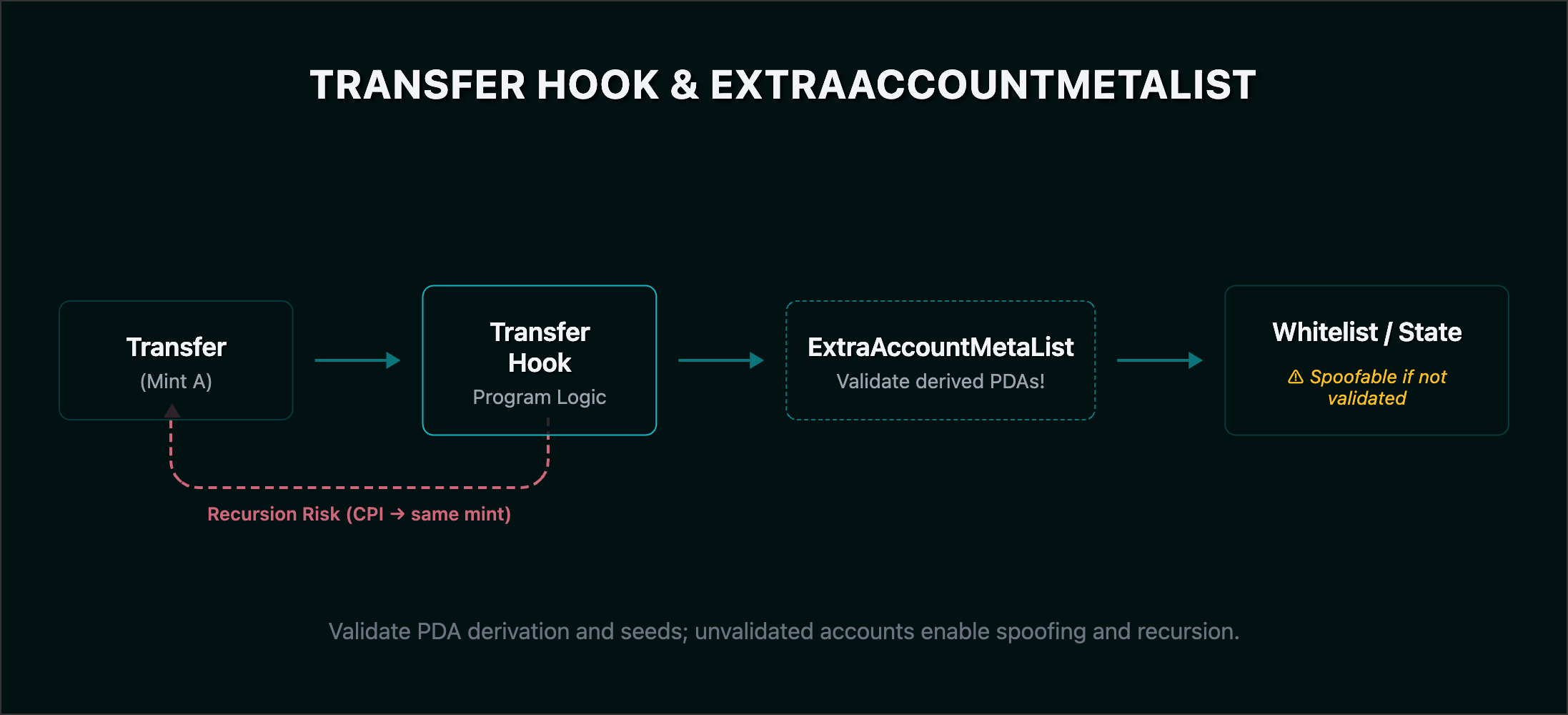
- Context Confusion & ExtraAccountMetaList: Hooks require additional accounts passed via an
ExtraAccountMetaList. Failure to strictly validate these seeds allows attackers to inject malicious accounts (e.g., a spoofed whitelist) to bypass transfer logic. - Infinite Recursion: If a Transfer Hook triggers a CPI that initiates another transfer of the same mint, it creates a recursion loop. While the runtime eventually halts this, it serves as a potent griefing vector to freeze assets.

1// 2026 Audit Pattern: Hook Validation2fn validate_hook_context(accounts: &[AccountInfo]) -> Result<()> {3 // 1. Verify ExtraAccountMetaList PDA derivation4 // 2. Enforce Principle of Least Privilege (ReadOnly on external state)5 // 3. Check CPI Depth (Solana limit is 4; deep hooks break DeFi composability)6 Ok(())7}
Confidential Balances: The use of ElGamal encryption and ZKPs in the Confidential Transfer extension necessitates auditing the Auditor Key. If this key is not set to
[0; 32], the protocol has a compliance backdoor that must be disclosed and its custody audited.The Economic Layer: Localized DoS (LDoS)
Solana's Localized Fee Markets (LFM) have eliminated global congestion but birthed the "Noisy Neighbor" attack. By flooding transactions that specifically write-lock a protocol's state accounts, an attacker can drive up priority fees for only that protocol.

For a full Solana security checklist including Token-2022 and PDAs, see our interactive guide.
- The Vector: An attacker can prevent liquidations by pricing out "keeper" bots during high-volatility events.
- State Sharding Requirement: High-throughput programs must move away from a single "Global State" PDA. Use sharded PDAs derived from user-specific seeds to minimize write-lock contention.
Technical Audit Requirement: Map the read/write dependency graph. If a single account is writable by >10% of traffic, it is a high-severity DoS vulnerability.
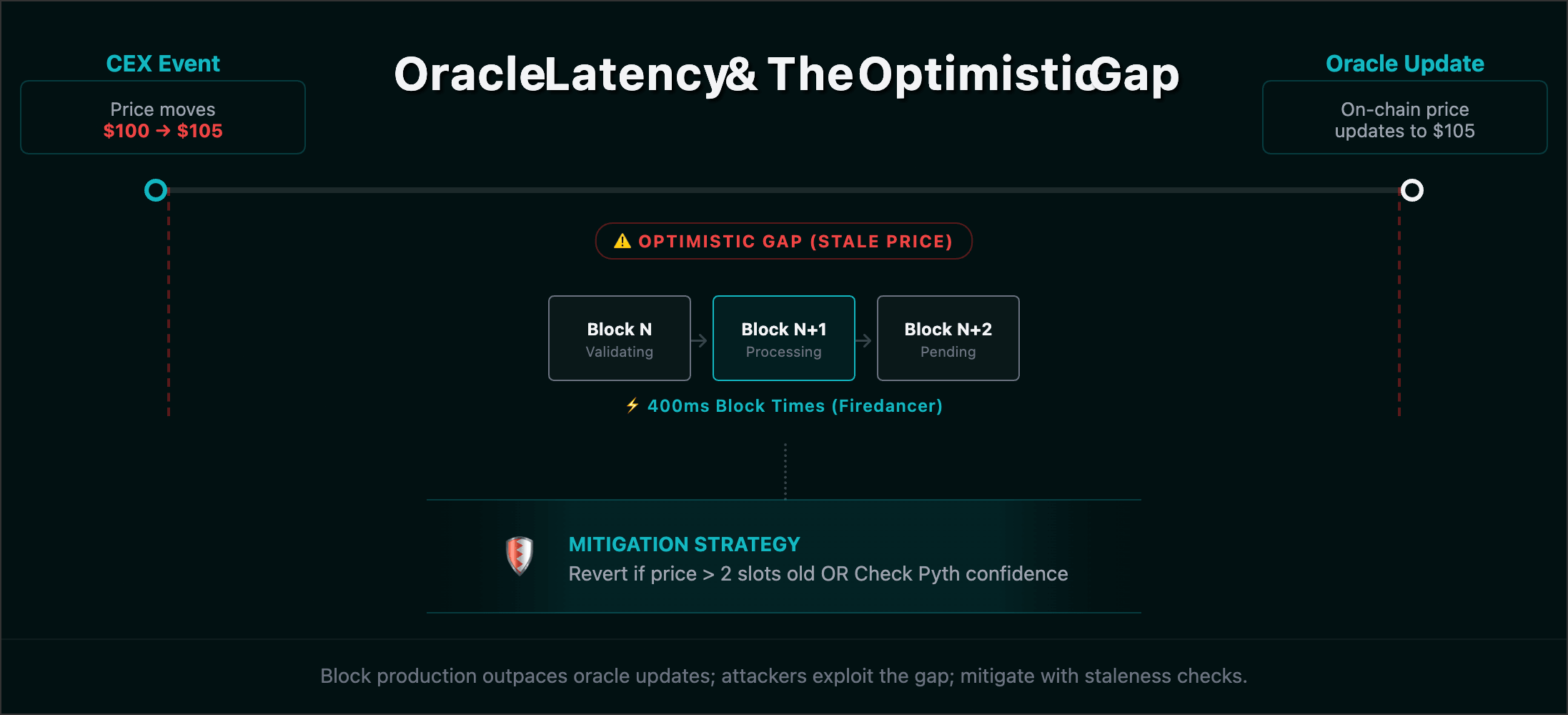
Oracle Latency and Flash Loan Atomicities
With Firedancer's 400ms blocks, block production now outpaces the update frequency of many decentralized oracles.

- Stale Price Attacks: Attackers can exploit the "Optimistic Gap" between a CEX price move and an on-chain oracle update.
- Mitigation: Protocols must implement Pyth Confidence Interval checks. If the interval is too wide or the
last_update_slotis more than 2 slots old, the instruction must revert.

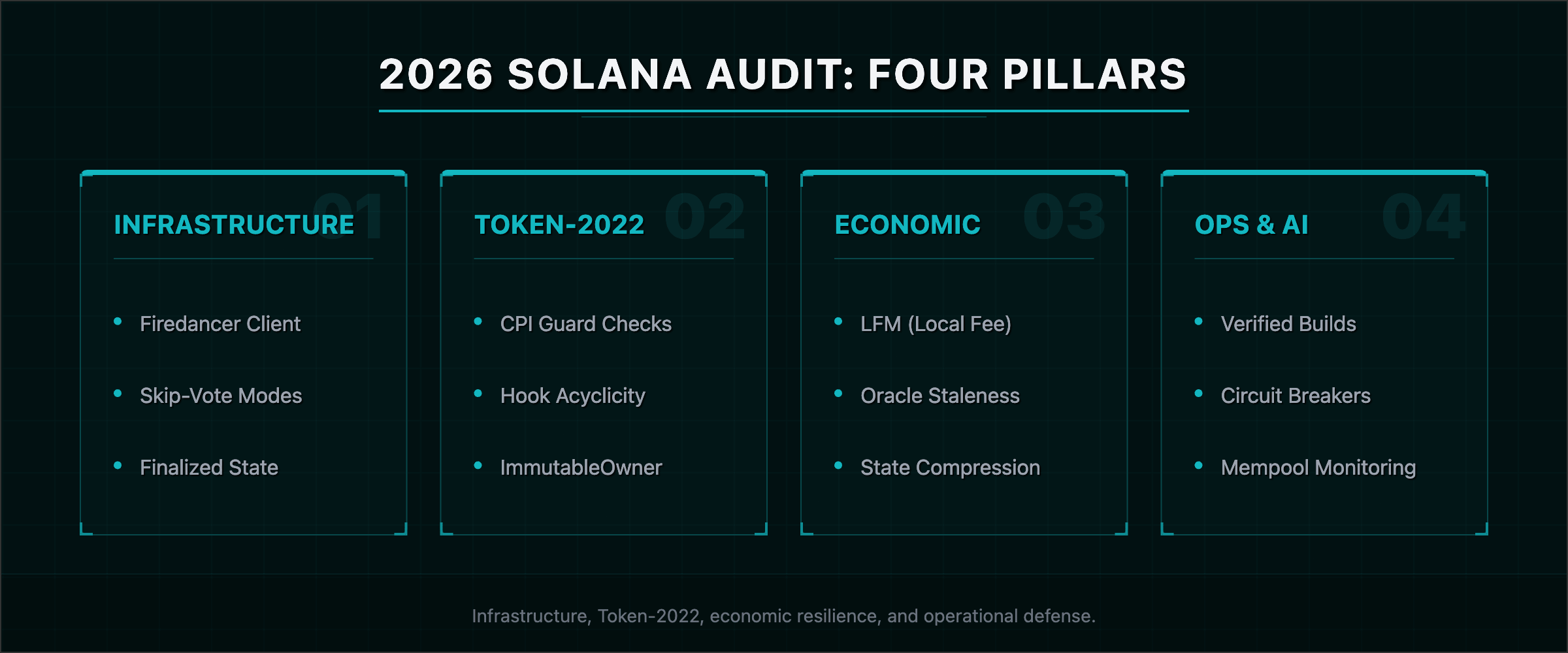
Master Security Checklist (2026 Framework)
1. Infrastructure Compliance
- Parallelization: Are accounts sharded to avoid Firedancer scheduler de-prioritization?
- Commitment Levels: Do irrevocable actions (bridge releases, large withdrawals) strictly require
Finalizedstatus? - Skip-Vote Resilience: Are timeouts/deadlines loose enough to handle finality delays from oversized blocks?
2. Token-2022 Implementation
- CPI Guard: Is
CpiGuardInstruction::Enableactive on all program-controlled vaults? - Hook Acyclicity: Is it mathematically impossible for a Transfer Hook to trigger an infinite loop?
- Immutable Ownership: Is
ImmutableOwnerenabled to prevent account hijacking?
3. Economic Resilience
- Priority Fee Awareness: Do off-chain bots implement dynamic bidding for Localized Fee Markets?
- Oracle Staleness: Does the logic revert if the price data is older than current_slot - 2?
- State Compression: If using compressed state, is there a decentralized Data Availability (DA) committee for Merkle tree reconstruction?
4. Operational & AI Defense
- Verified Build: Is the program hash registered on-chain and deterministically buildable?
- Circuit Breakers: Is there a functional multisig (e.g., Squads) with a timelocked pause mechanism?
- Autonomous Monitoring: Is an AI agent (e.g., SOLSEC) monitoring the mempool for flash-loan-funded exploit patterns?
Get in touch
At Zealynx, we specialize in Solana smart contract audits that account for Firedancer, Token-2022, and localized fee markets. Our 2026 framework aligns with the checklist above, from skip-vote resilience to transfer-hook validation and LFM-aware design. Smart contract security is no longer syntax-only; it's systemic.
Get a Solana audit quote or review our pre-audit checklist to prepare your program for a thorough review.
FAQ: Solana Audit 2026 & Security
1. How much does a Solana smart contract audit cost in 2026?
Solana smart contract audits in 2026 typically cost 20–30% more than equivalent Ethereum audits due to a smaller pool of Rust/Solana experts. Expect $60,000–$130,000 for standard Solana DeFi protocols and $180,000+ for complex programs (Token-2022-heavy, Firedancer-aware, or bridge-related). Simple Solana program audits start at $7,000–$20,000. Pricing reflects logic density, Token Extensions usage, and whether your design accounts for skip-vote risk and localized fee markets. See our audit pricing guide for full benchmarks.
2. What is Firedancer and why does it change Solana audit requirements?
Firedancer is a high-performance Solana validator client that moves the network's performance limit to the hardware layer. With SIMD-0370, block sizes are no longer rigidly capped by Compute Units (CUs), high-performance leaders can produce very large blocks. Weaker validators (older hardware or the Agave client) may fail to process these blocks within the 400ms slot and skip voting instead of halting. That creates verification lag: your transaction might be included quickly but finalize later, exposing protocols that assume 400ms finality (e.g. liquidations, oracles) to micro-reorgs or bridge-latency risk. Audits in 2026 must check time-sensitive logic for
valid-until-slot and slippage tolerances that account for this variance.3. What is Token-2022 and what are transfer hook security risks?
Token-2022 (Token Extensions) is the extended Solana token standard that adds features like Transfer Hooks, custom program logic that runs on every transfer of a mint. Transfer hooks receive extra accounts via an ExtraAccountMetaList; if PDA derivation and seeds aren't strictly validated, attackers can inject malicious accounts (e.g. a spoofed whitelist) and bypass transfer logic. Hooks can also trigger CPI (cross-program invocations) that initiate another transfer of the same mint, causing infinite recursion or griefing that freezes assets. Audits must verify hook acyclicity, least-privilege on external state, and CPI depth limits. Token-2022 and transfer hooks are defined in our glossary.
4. What are localized fee markets (LFM) and the "noisy neighbor" attack on Solana?
Localized Fee Markets (LFM) replace Solana's old global congestion model: fees are now tied to which accounts are contended. An attacker can flood transactions that write-lock your protocol's state accounts, driving up priority fees only for your protocol, the "noisy neighbor" attack. Keepers and liquidator bots can be priced out during volatility, so liquidations fail. Audits should map the read/write dependency graph: if a single account is writable by more than ~10% of traffic, it's a high-severity DoS vector. High-throughput programs should use sharded PDAs (user-derived seeds) instead of a single global state account to reduce contention.
5. What is verification lag or skip-vote risk on Solana?
Verification lag (or skip-vote risk) occurs when Firedancer leaders produce very large blocks that slower validators cannot process within the 400ms slot. Those validators skip voting rather than halt, so consensus finality is delayed for transactions in those blocks. If your protocol assumes 400ms finality for liquidations, oracle updates, or bridge releases, you're exposed to a window where your tx is "included" but not yet finalized, enabling micro-reorgs or bridge-latency exploits. Audits must ensure time-sensitive instructions use
valid-until-slot checks and slippage tolerances that account for slot-based timing variance, and that irrevocable actions require Finalized commitment level where appropriate.6. What should a 2026 Solana audit checklist include?
A 2026 Solana audit checklist should cover: (1) Infrastructure, account parallelization for Firedancer, commitment levels (Finalized) for bridge/withdrawals, skip-vote resilience in timeouts; (2) Token-2022, CPI Guard and ImmutableOwner on vaults, transfer-hook acyclicity, Auditor Key review for Confidential Transfer; (3) Economic resilience, priority-fee–aware bots for LFM, oracle staleness (revert if price > 2 slots old), state compression/DA if used; (4) Operational, verified build, circuit breakers (e.g. Squads multisig + timelock), and mempool monitoring for flash-loan–style exploit patterns. Our Solana security checklist and audit pricing 2026 posts align with this framework.