Back to Blog 

RWADeFi
Why ERC-20 Fails for Tokenized Securities: The Compliant RWA Standard
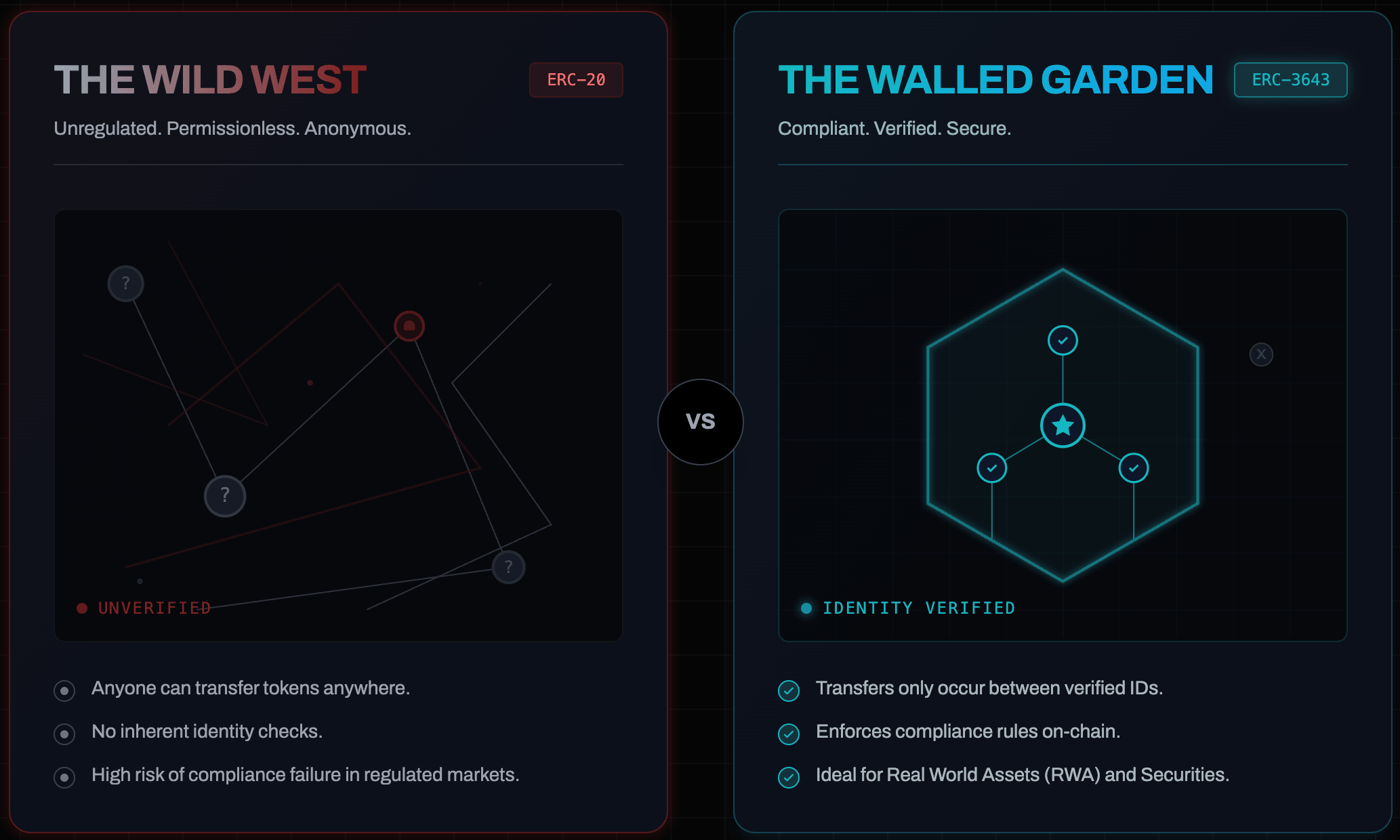
If you are building DeFi protocols, ERC-20 is the gold standard. It creates maximum liquidity and composability because it is permissionless: any address can send tokens to any other address.
However, if you are engineering solutions for Real World Assets (RWA)—such as tokenized equity, debt, or real estate—the "permissionless" nature of ERC-20 is a fatal architectural flaw.
Regulations (Reg D, MiFID II, etc.) require you to know who holds your asset at all times. In a standard ERC-20 architecture, you lose control the moment the token hits a secondary market (DEX). You cannot natively prevent a verified investor from selling your security token to a sanctioned entity or an unaccredited wallet.
Attempts to fix this usually involve centralized "envelopes" or whitelists managed by a single private key, which reintroduces single points of failure and centralization risks that blockchain was meant to solve. You need a way to enforce complex regulatory logic on-chain without sacrificing the security of a public ledger.
The end result: A "walled garden" on public infrastructure
By implementing ERC-3643 (formerly the T-REX protocol), you decouple the asset from the identity.

At the end of this implementation, you will have a smart contract system where:
- Compliance is proactive, not reactive: Unauthorized transfers revert automatically before state changes occur.
- Identity is portable: Users utilize a decentalized identity (ONCHAINID) rather than just a wallet address.
- Rules are modular: You can swap compliance rules (e.g., "block US investors") without redeploying the token.
You effectively build a permissioned sub-layer within public chains like Ethereum or Polygon, leveraging global infrastructure while maintaining institutional-grade compliance.
The steps: Architecting compliant token systems
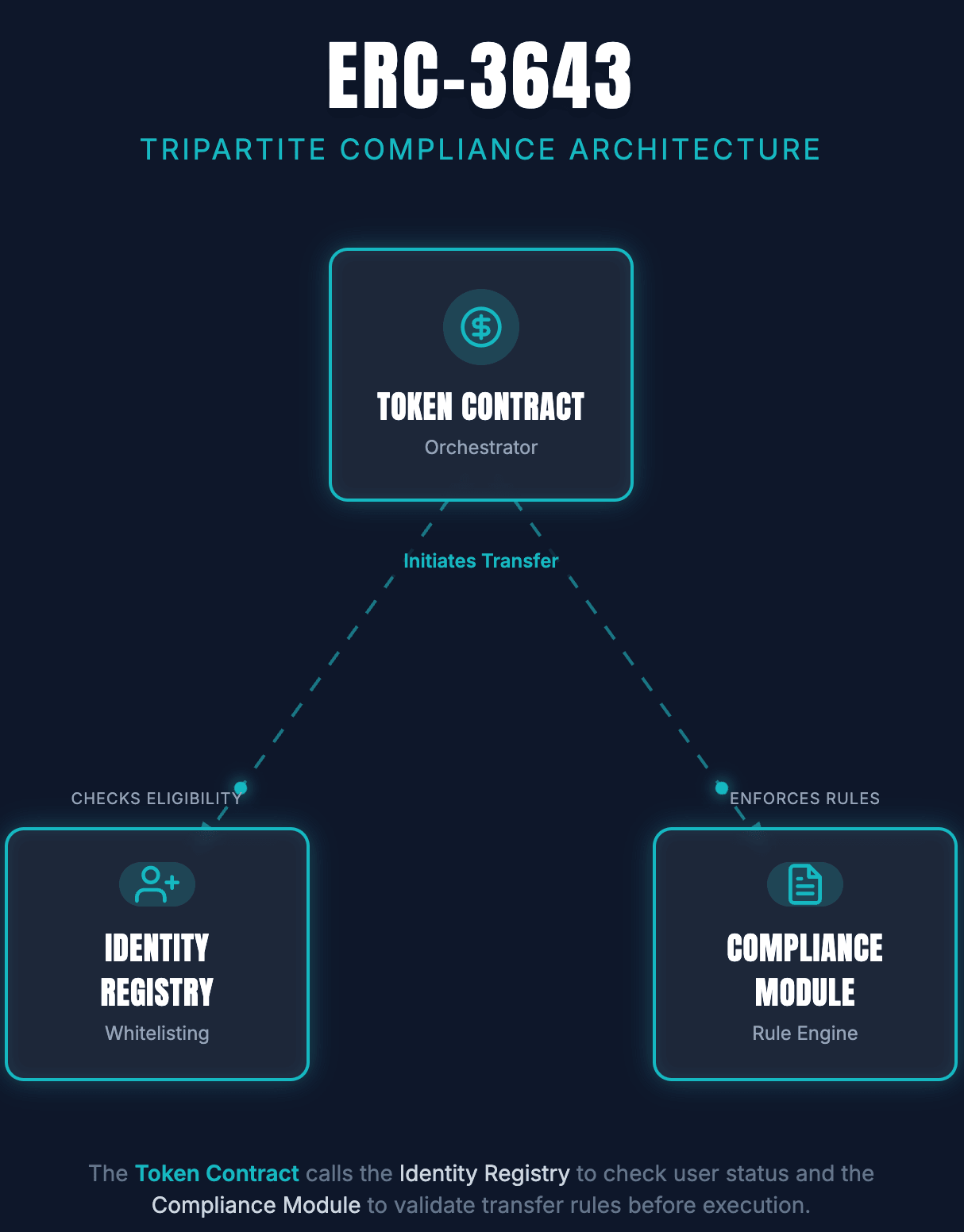
1. Architect the tripartite system
Do not build a monolithic contract. ERC-3643 relies on a separation of concerns to manage complexity and gas costs. You must deploy three distinct interacting layers:

- The Token Contract: Maintains balances and standard ERC-20 interfaces (for wallet compatibility) but overrides transfer logic.
- The Identity Registry: Acts as the source of truth, mapping wallet addresses to verified On-Chain Identities.
- The Compliance Module: Stores the rule sets (logic) that dictate who can hold the token and when.
2. Decouple identity from wallet addresses
Standard whitelists are fragile; if a user loses their private key, they lose their identity. To solve this, you must implement ONCHAINID (based on ERC-734 and ERC-735).
Deploy an Identity Contract: This contract represents the user. It holds "Keys" (management or action keys) and "Claims" (hashes of verified data).
Store Claims On-Chain, Data Off-Chain: Do not store PII (names, passports) on the blockchain. Instead, a trusted 3rd party signs a hash (a Claim) validating the user (e.g., "KYC Cleared"). The Identity Registry checks for this cryptographic proof, not the raw data.
Allow Key Rotation: If a user's wallet is compromised, they can revoke the wallet key via the Identity Contract without losing their accumulated credentials/claims.
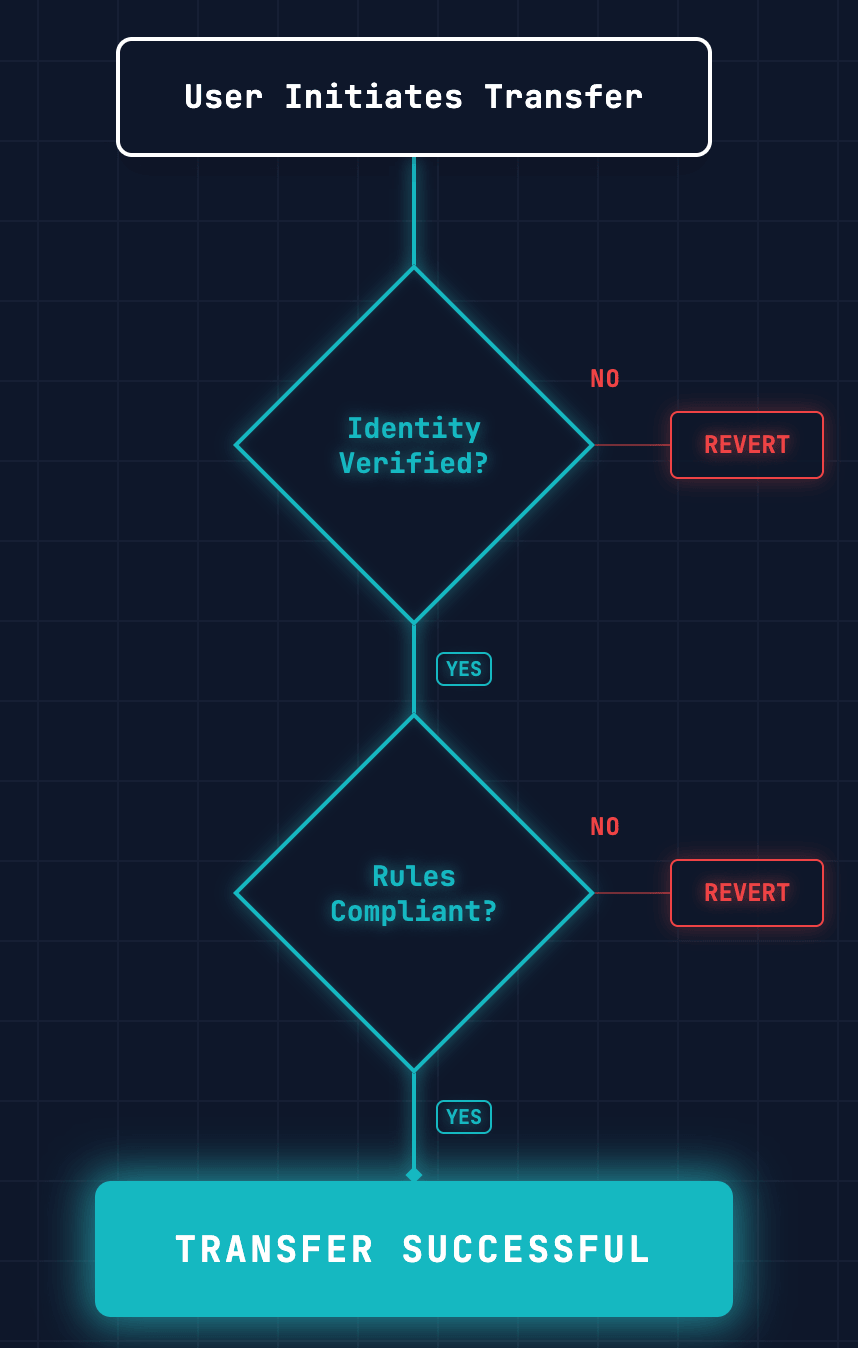
3. Intercept and validate transfers
You must override the standard
transfer and transferFrom functions. Instead of immediately updating balances, your contract must execute a conditional check against the other two layers.The logic flow you must implement is:

- Trigger: Wallet A attempts to send 100 tokens to Wallet B.
- Identity Check: The Token calls IdentityRegistry. Is Wallet B linked to a verified ONCHAINID?
- Compliance Check: The Token calls ModularCompliance. Does this specific transaction violate any active rules (e.g., volume limits, country bans)?
- Execution:
- If Both True: Update balances.
- If Any False: Revert transaction.
This ensures that non-compliant transfers are technically impossible at the protocol level.
4. Configure pluggable compliance modules
Hardcoding compliance rules leads to technical debt. Regulations change. Use the
ModularCompliance contract to plug in specific logic modules.Common modules you can deploy include:
- CountryAllowModule: Checks the investor's Identity country code against a list of sanctioned nations.
- MaxHoldersModule: Enforces a hard cap on the number of token holders (critical for exemptions like the 2,000-investor rule in the US).
- VolumeRestrictionModule: Prevents "dumping" by limiting the percentage of a balance that can be moved within a specific timeframe.
Because these are modular, you can upgrade a rule by pointing the Token Contract to a new Compliance Module address without migrating user balances.
5. Implement governance and recovery mechanisms
Unlike Bitcoin, regulated securities require recourse. You must implement the
IAgentRole interface.- Forced Transfer: In the event of a lost key or court order, an authorized Agent must be able to move tokens from a lost wallet to a new one.
- Freezing: Agents must be able to pause token transfers globally or freeze specific suspicious wallets.
Security Note: To mitigate the "Superuser" risk, the Agent role should always be assigned to a Multi-Sig wallet (e.g., Gnosis Safe) or an MPC custody solution, never a single private key.
Next steps
ERC-3643 allows you to write code that satisfies legal teams without building a centralized database. To start building:
- Review the standard: Read the finalized EIP-3643 documentation for the exact interface specifications.
- Audit the code: Review the reference implementations provided by the ERC-3643 Association.
- Test on Sepolia: Deploy a mock Identity Registry and try to transfer tokens between a verified and unverified account to see the revert logic in action.
Get in touch
At Zealynx, we specialize in architecting compliant tokenization systems for the financial sector. Whether you are transitioning to a Permissioned DeFi model, need an audit for your ERC-3643 contracts, or require a strategy to tokenize Real World Assets securely, our team is ready to assist — reach out.
Want to stay ahead with more in-depth analyses like this? Subscribe to our newsletter and ensure you don’t miss out on future insights.
FAQ: Understanding compliant token systems
1. Why is ERC-20 insufficient for Real World Assets?
The core limitation of ERC-20 is its permissionless nature. Once a token is sent to a wallet, the protocol loses control over where it goes next. For regulated assets like securities, you are legally required to know and restrict who holds the asset at all times, making the "anyone-to-anyone" transfer logic of ERC-20 a regulatory liability.
2. What is KYC and why is it required for tokenized securities?
KYC (Know Your Customer) is the regulatory process of verifying an investor's identity. For tokenized securities, you must cryptographically prove that a wallet belongs to a verified, accredited investor before they can hold your asset. ERC-3643 stores this proof as a "Claim" on the user's ONCHAINID, not directly on the blockchain, keeping personal data private while maintaining compliance.
3. What is ONCHAINID and how does it protect my identity?
ONCHAINID is a smart contract that represents you (not your wallet). It stores cryptographic proofs (Claims) that you've been verified by a trusted party, while your actual personal data stays off-chain. If you lose your wallet, you can link a new wallet address to your existing ONCHAINID without re-doing KYC, making your identity portable and recoverable.
4. What is the difference between whitelisting and ERC-3643?
A simple whitelist is often centralized and links identity directly to a wallet address. If a standard whitelist user loses their key, they lose their identity. ERC-3643 detaches identity from the wallet. It uses a decentralized identity system (ONCHAINID) where a user can rotate their wallet keys without losing their verified status or claims, offering a much more robust and recoverable system.
5. How does ERC-3643 work with DEXs (Decentralized Exchanges)?
Traditional DEXs like Uniswap are permissionless and incompatible with ERC-3643 by design. However, you can build compliant AMMs that check the Identity Registry before allowing trades, creating a "permissioned DEX" where only verified participants can swap your security tokens. This maintains compliance while enabling secondary market liquidity within your regulated ecosystem.
6. Is the compliance logic upgradeable?
Yes. One of the strongest features of this standard is its modularity. The rules that dictate who can hold the token are stored in a separate
ModularCompliance contract. If regulations change (e.g., a new country is sanctioned), you can deploy a new compliance module and point the token to it, instantly updating the rules for all future transfers without needing to migrate or reissue the tokens.Glossary
| Term | Definition |
|---|---|
| Security Token | Blockchain-based representation of regulated securities (equity, debt, real estate) requiring transfer restrictions and investor verification under securities law. |
| Identity Registry | ERC-3643 component acting as source of truth, mapping wallet addresses to verified on-chain identities and enabling compliance checks before transfers. |
| Modular Compliance | Pluggable smart contract architecture allowing regulatory rules (country bans, holder limits) to be updated without redeploying the token contract. |
| On-Chain Identity | Decentralized identity system (ONCHAINID) based on ERC-734/735 that decouples user identity from wallet addresses, enabling key rotation and portable credentials. |
| Permissioned DeFi | Regulated sub-layer on public blockchains where only verified participants can interact, combining institutional compliance with decentralized infrastructure. |