Back to Blog 
 \"M3D"
\"M3D" 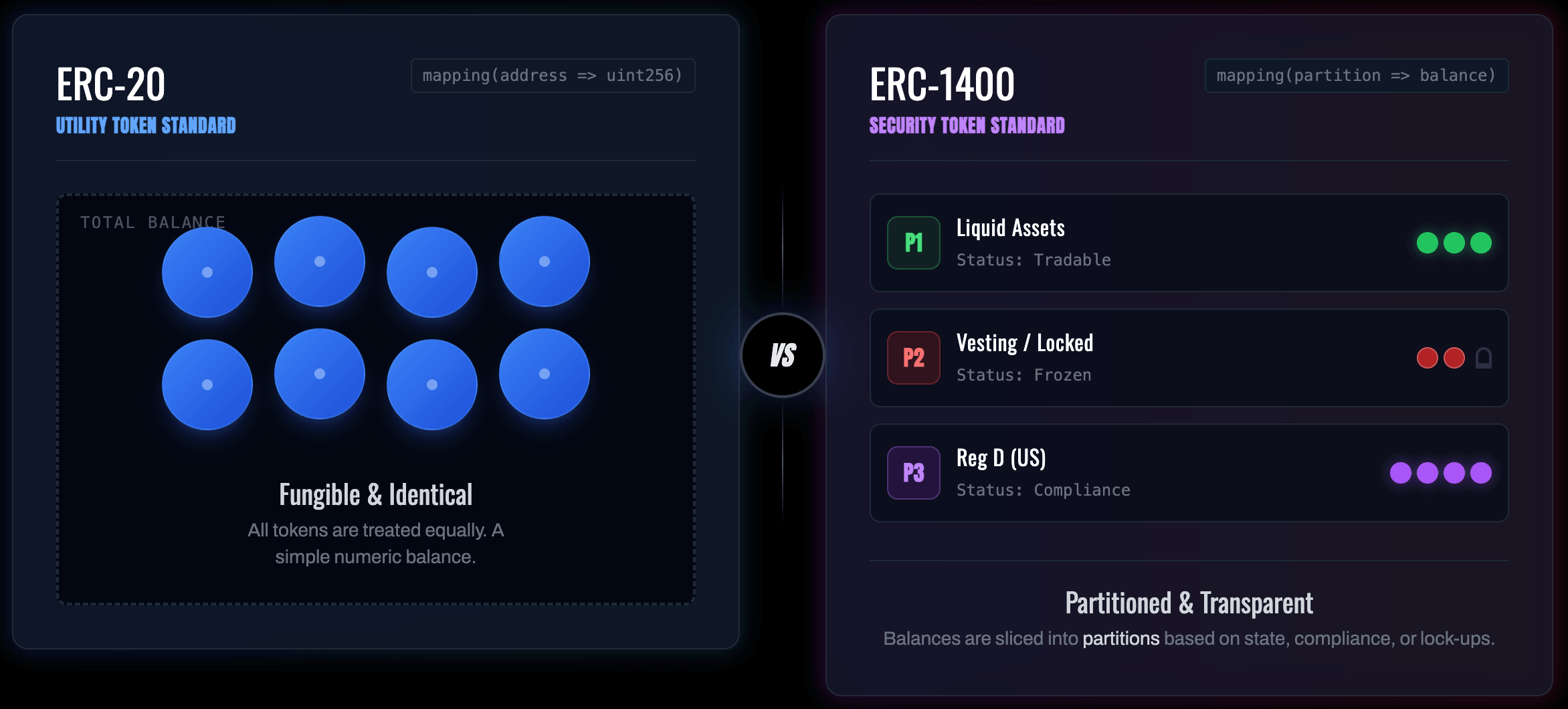

RWAWeb3 Security
ERC-1400 Explained: Security Token Standard for RWA

8 min
32 views
The promise of tokenizing "Real World Assets" (RWA) often hits a brick wall when it meets the reality of financial regulation. While the ERC-20 standard democratized token creation, its architectural simplicity is its greatest weakness when applied to regulated securities.
For a developer, a security is not just a balance; it is a complex state machine governed by legal constraints, lock-up periods, and jurisdictional rules. ERC-1400 (and its sub-standards) was designed to move these requirements from external spreadsheets into the smart contract storage layout.
The context: Why ERC-20 fails regulated assets
The fundamental data structure of an ERC-20 contract is a simple mapping:
1mapping(address => uint256) private _balances;
This "agnostic" approach assumes every unit of a token is identical to every other unit. However, in capital markets, shares are often restricted by when they were issued. For example, a founder’s shares might be subject to a 12-month lock-up (e.g., SEC Rule 144), while secondary market shares are liquid.
Under ERC-20, representing these two classes would require two separate contracts, which fragments liquidity and complicates the cap table. Furthermore, the
transfer function is binary: if the sender has the balance, the transaction succeeds. There is no native hook to verify if the recipient is KYC-cleared or if the transfer violates a daily volume limit.The solution: A modular architecture for securities

ERC-1400 isn't a single contract; it’s a suite of standards that work together to manage the lifecycle of a regulated asset.
1. Partial fungibility (ERC-1410)
This is the most significant architectural shift. Instead of a flat mapping, ERC-1410 uses nested mappings to create "partitions" or tranches of tokens.
1// Traditional ERC-202mapping(address => uint256) balances;34// ERC-1410 Partitions5mapping(address => mapping(bytes32 => uint256)) partitionBalances;
Each
bytes32 key represents a partition (e.g., keccak256("LOCKED")). This allows a single address to hold tokens with different legal properties.The Storage Trade-off:
As developers, we must acknowledge the gas overhead here. Since Ethereum mappings are not iterable, we have to maintain an auxiliary array of partition keys for each user (
mapping(address => bytes32[]) userPartitions). Every time a user interacts with a new partition, you incur a SSTORE cost for the mapping and an array push. For high-volume trading, this "gas tax" is the price of on-chain compliance.
2. Programmable validation
ERC-1594 introduces the
canTransfer and canTransferByPartition view functions. These allow UIs and other contracts to simulate a transfer and receive a status code (based on EIP-1066) explaining why a transfer might fail (e.g., 0x56 for "Invalid Sender").
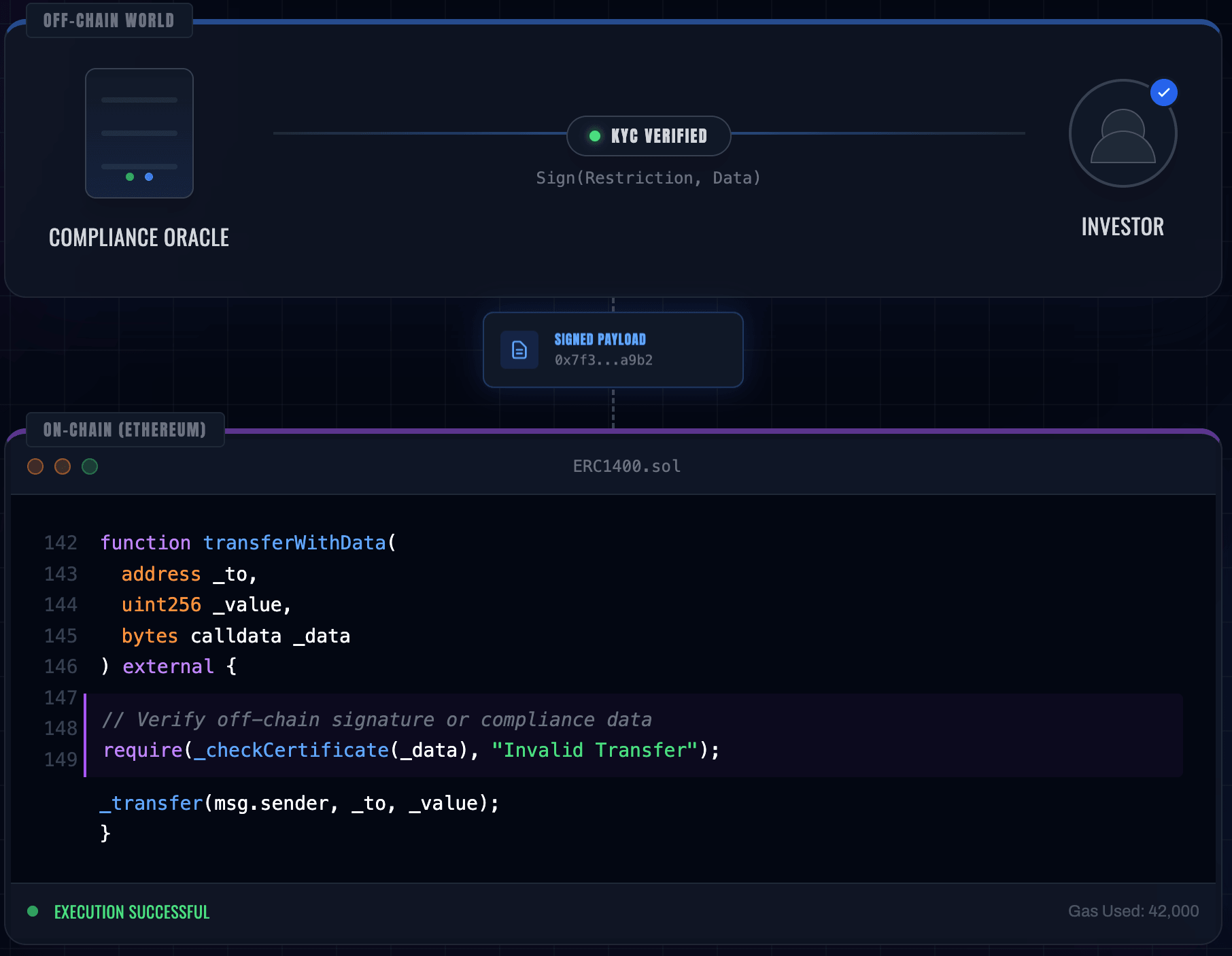
The most powerful tool here is
transferWithData:1function transferWithData(address to, uint256 value, bytes data) public;
The
bytes data field allows for "Off-chain Injection." A compliance server can sign a "permission certificate" off-chain, which the user then passes into the contract. The contract recovers the signer's address, validates the cryptographic proof, and executes the transfer. This balances the privacy of sensitive KYC data with the finality of on-chain execution.3. Document and controller management (ERC-1643 & ERC-1644)
- ERC-1643: Solves the "legal link" problem. It allows you to attach document hashes (IPFS/CID) directly to the token. If the legal memorandum changes, the hash update is recorded on-chain, creating an immutable audit trail.
- ERC-1644: Introduces the "Controller" role. This allows for forced transfers. While this feels antithetical to the "not your keys, not your coins" ethos, it is a non-negotiable requirement for legal compliance (e.g., court-ordered asset seizures or lost private key recovery).
Implementation pitfalls and security
Implementing ERC-1400 introduces unique attack vectors that don't exist in standard DeFi tokens.
The "bypass" vulnerability
A common implementation error is applying compliance logic to
transferByPartition but leaving the standard transfer (inherited from ERC-20) wide open.
Solution: Ensure all transfer entry points pipe through a single internal _verifyTransfer hook that checks all partitions and compliance certificates.Controller key risk
The
ERC-1644 controller role is a "god mode" key. If compromised, an attacker can drain any wallet.Mitigation:
- Multi-Sig: The controller should never be an EOA. It must be a Gnosis Safe or similar multi-signature contract.
- Timelocks: Implement a 48-hour delay on controller actions to allow for community alerts or legal intervention.
Real-world use cases
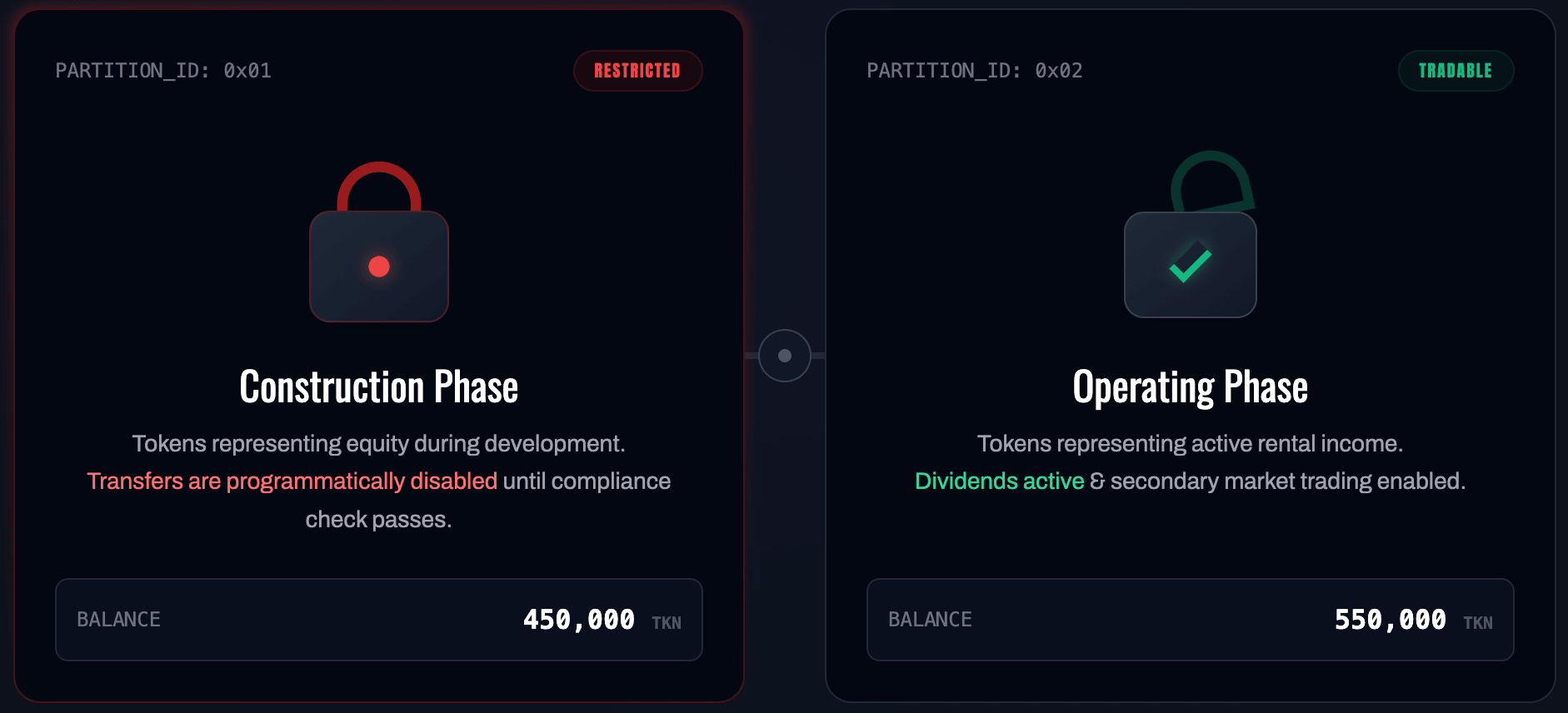
Real estate tokenization
An issuer can use partitions to manage different phases of a project. Tokens in "Phase A" (Construction) could be non-transferable and excluded from dividend distributions. Once the building is operational, the issuer can migrate those tokens to a "Phase B" (Operating) partition, which allows for transferability and rent-payout eligibility.
Jurisdictional management (Reg D vs. Reg S)
For U.S.-based issuers, you can segregate domestic investors (subject to a 1-year lock-up) and international investors (subject to a 40-day lock-up) within the same contract using two distinct partitions. A time-based oracle or internal logic can then "unlock" these partitions automatically as they mature.
Summary: Choosing your standard
| Feature | ERC-20 | ERC-1400 | ERC-3643 (T-REX) |
|---|---|---|---|
| Fungibility | Total | Partial (Partitions) | Total (Restricted by Identity) |
| Compliance | External | Native (ERC-1594) | Modular (Compliance Modules) |
| Identity | None | Data-Agnostic | Mandatory (ONCHAINID) |
| Gas Cost | Low | High | Medium |
ERC-1400 is not a "plug-and-play" solution. It requires a deep understanding of storage layouts and a willingness to handle higher gas costs in exchange for granular, automated legal compliance. For developers building the next generation of institutional finance, it remains the most flexible framework available on the EVM.
Get in touch
At Zealynx, we understand that tokenizing real world assets requires more than just Solidity—it requires a robust architecture that bridges the gap between legal frameworks and blockchain state. Whether you are building an RWA platform, implementing ERC-1400 for compliance, or auditing a tokenized asset infrastructure, our team is ready to assist — reach out.
Want to stay ahead with more in-depth analyses like this? Subscribe to our newsletter and ensure you don’t miss out on future insights.
FAQ: ERC-1400 & security standard
1. What is the difference between ERC-1400 and ERC-20?
ERC-20 assumes all tokens are identical (fungible) and doesn't enforce transfer restrictions natively. ERC-1400 is designed for securities: it allows for "partial fungibility" (partitions) to separate different classes of shares (e.g., locked vs. unlocked) and includes native hooks to enforce compliance rules (KYC/AML) before a transfer can occur.
2. Why is "partial fungibility" important for RWAs?
In traditional finance, not all shares are equal. Some are subject to lock-up periods (Regulation D), while others are freely tradable. "Partial fungibility" allows a single contract to recognize these differences, preventing a locked share from being sold on a secondary market while allowing liquid shares to trade freely.
3. What is "off-chain injection"?
It's a mechanism where a trusted off-chain server grants permission for a specific transaction by signing a piece of data. The user includes this signed data when calling the smart contract. This allows the contract to verify complex regulatory requirements (like "is this user an accredited investor?") without storing sensitive personal data on the public blockchain.
4. Is ERC-1400 compatible with ERC-20 wallets?
Yes. ERC-1400 is designed to be backwards compatible. Most implementations inherit from the ERC-20 standard, meaning an ERC-1400 token will show up in MetaMask or hardware wallets just like any other token, although advanced features (like partition management) may require a custom dApp interface.
5. What are security tokens and why do they need special standards?
Security tokens are blockchain-based representations of traditional financial securities like stocks, bonds, or real estate shares. Unlike utility tokens or cryptocurrencies, they are subject to securities regulations (SEC in the U.S., MiFID II in EU). They need special standards like ERC-1400 because regulations require features that standard ERC-20 tokens cannot provide: investor accreditation checks (KYC/AML), transfer restrictions based on jurisdiction or holding periods, forced transfers for legal compliance, and the ability to enforce lock-up periods on specific share classes.
6. What are Regulation D and Regulation S lock-up periods?
Regulation D and Regulation S are SEC exemptions that allow companies to raise capital without full public registration. Regulation D applies to U.S. investors and typically requires a 1-year lock-up period before shares can be resold. Regulation S applies to offerings made outside the U.S. to non-U.S. investors and typically has a 40-day lock-up. ERC-1400 partitions allow issuers to enforce these different lock-up periods within a single smart contract, automatically unlocking shares when the regulatory time period expires without requiring manual intervention.
Glossary
| Term | Definition |
|---|---|
| Partial Fungibility | Token architecture where units within the same contract can have different properties, enabling distinct share classes with separate transfer rules. |
| Token Partition | Named tranche (bytes32 key) within ERC-1410 tokens separating shares by legal status such as locked, vested, or freely tradable. |
| Off-Chain Injection | Pattern where compliance servers sign permission certificates off-chain that users pass into smart contracts for on-chain validation. |
| Controller Role | ERC-1644 privileged address with forced transfer capability for legal compliance scenarios like court orders or lost key recovery. |
| Cap Table | Capitalization table recording all token holders, their share classes, and ownership percentages for corporate governance and compliance. |

