Back to Blog 

AuditWeb3 Security
Smart Contract Audit ROI: Investor Due Diligence Guide
In Web2, a critical bug usually results in a patch and a support ticket. In Web3, a bug is often a binary event: either your protocol works, or it is mathematically zeroed out in a single block.
For a technical founder or CTO heading into a Series A, security is no longer a post-funding checklist item. It is the primary filter through which institutional investors view your project. When a investor performs Technical Due Diligence (TechDD), they aren’t just looking at your code; they are evaluating your team's culture of risk, your operational discipline, and your long-term viability.
Here is how sophisticated investors actually dissect your audit history and what you need to have in place before you open the data room.
Why the Name on the PDF Matters
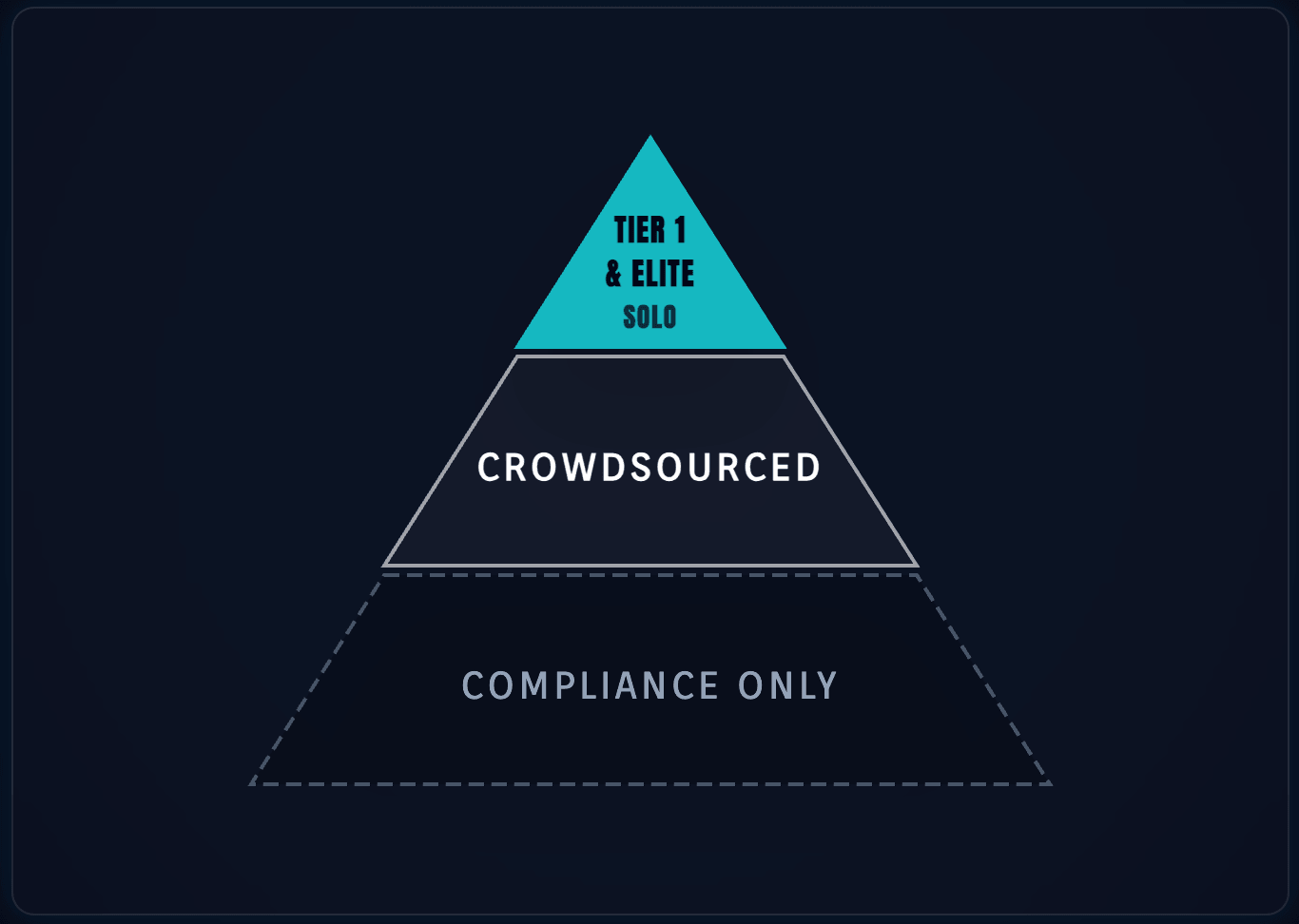
In the investor’s eyes, not all audits are created equal. The smart contract audit services you choose signal your project’s capitalization and your team's foresight. The industry has stratified into a clear hierarchy of trust:
- Tier 1 Firms (The Institutional Standard): Firms like OpenZeppelin, Trail of Bits, or Spearbit are viewed as the "Gold Standard." An audit from these firms acts as a reputational insurance policy for the investor. It shows you have the capital to pay for elite talent and the patience to wait for their months-long queues.
- Solo Elite Auditors: For Seed-stage projects, a review by a recognized solo auditor (e.g., Pashov or Trust) is increasingly accepted. It shows agility and a proactive stance toward security without burning through your entire runway before product-market fit.
- Competitive Audits (Crowdsourced): Platforms like Code4rena or Sherlock are viewed as excellent "breadth" layers. Investors like these because they incentivize hundreds of eyes to find edge cases that a small team might miss.
- Boutique Specialist Firms: Agile teams like Zealynx serve as a high-ROI "boutique addition" to this stack. Investors value them for providing the deep architectural collaboration of a Tier 1 firm with the speed and personalized focus of a solo auditor—ensuring your remediation commits are verified and solid.

The "Stamp" Trap: If your audit history consists only of "budget" firms that provide 48-hour turnarounds, sophisticated VCs will notice. A significantly lower smart contract audit price often signals a "compliance-only" mindset—where the goal is to get a badge for the website rather than to actually secure the protocol.
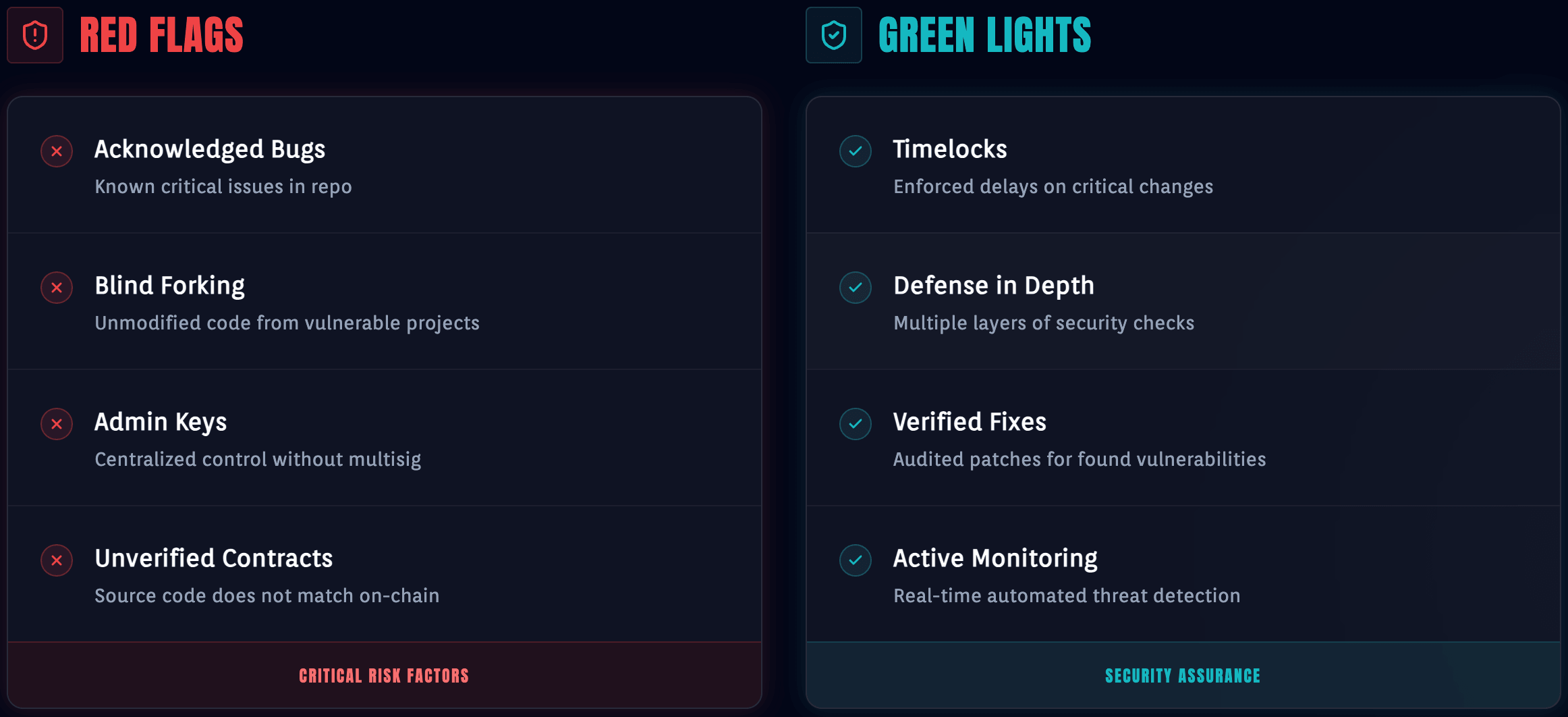
Red Flags: Behavioral Signs of Lazy Engineering
Investors look for "code smells" that suggest a lack of engineering rigor. These are often deal-breakers during the TechDD phase:

- The "Acknowledged" Status: When an audit report lists a "High" or "Critical" vulnerability as "Acknowledged" rather than "Fixed," it’s a massive warning. It tells the investor you are comfortable with existential risk. Unless there is a massive governance constraint (like a Timelock) in place, an unfixed "Acknowledged" risk is a disqualifier.
- Blind Forking (Copy-Paste Engineering): Investors use tools to check for code similarity. If 95% of your code is a fork of a known protocol but you haven’t audited the 5% of changes you made, you are seen as a high-risk liability.
- Centralization in Disguise: If your protocol claims decentralization but a single Externally Owned Account (EOA) has the power to mint tokens or pause the protocol without a multi-sig or timelock, you have a "rug pull" vector.
Anatomy of an Audit: Reading Between the Lines
When an investor opens your security folder, they are looking for a timeline, not a one-off event. They scan specific sections to determine the "health" of the engagement:
- Verification of Scope: Did the audit cover your core business logic (staking, lending, or vaults), or just a standard ERC-20 token? Hiding the scope is a common but easily spotted tactic.
- Bug Density at First Review: If the first draft of an audit finds 15 "Critical" bugs, it tells the investor your team uses auditors as a Quality Assurance (QA) department. They want to see a clean initial submission that reflects strong internal testing.
- The Remediation Trail: Investors want to see the specific commit hashes where bugs were fixed and subsequently verified by the auditor.
- Code Hygiene: Lack of NatSpec documentation or inconsistent variable naming signals that the codebase will be a maintenance nightmare. To a technical investor, messy code is inherently insecure code.
The Technical Checklist: High-Risk Solidity Patterns
During TechDD, investors (or their technical partners) will look for specific patterns that indicate whether a developer understands the adversarial nature of the EVM:
- Reentrancy Protection: Use of
ReentrancyGuardand adherence to the Checks-Effects-Interactions pattern. - Access Control: Clear separation of roles (RBAC) rather than a single
Ownableaddress. - Oracle Integrity: Ensuring the protocol doesn't rely on a single DEX spot price, which is vulnerable to flash loan manipulation.
- Upgradeability: If the contracts are proxies, there must be a Timelock (24–48 hours) to prevent "instant" malicious logic changes.
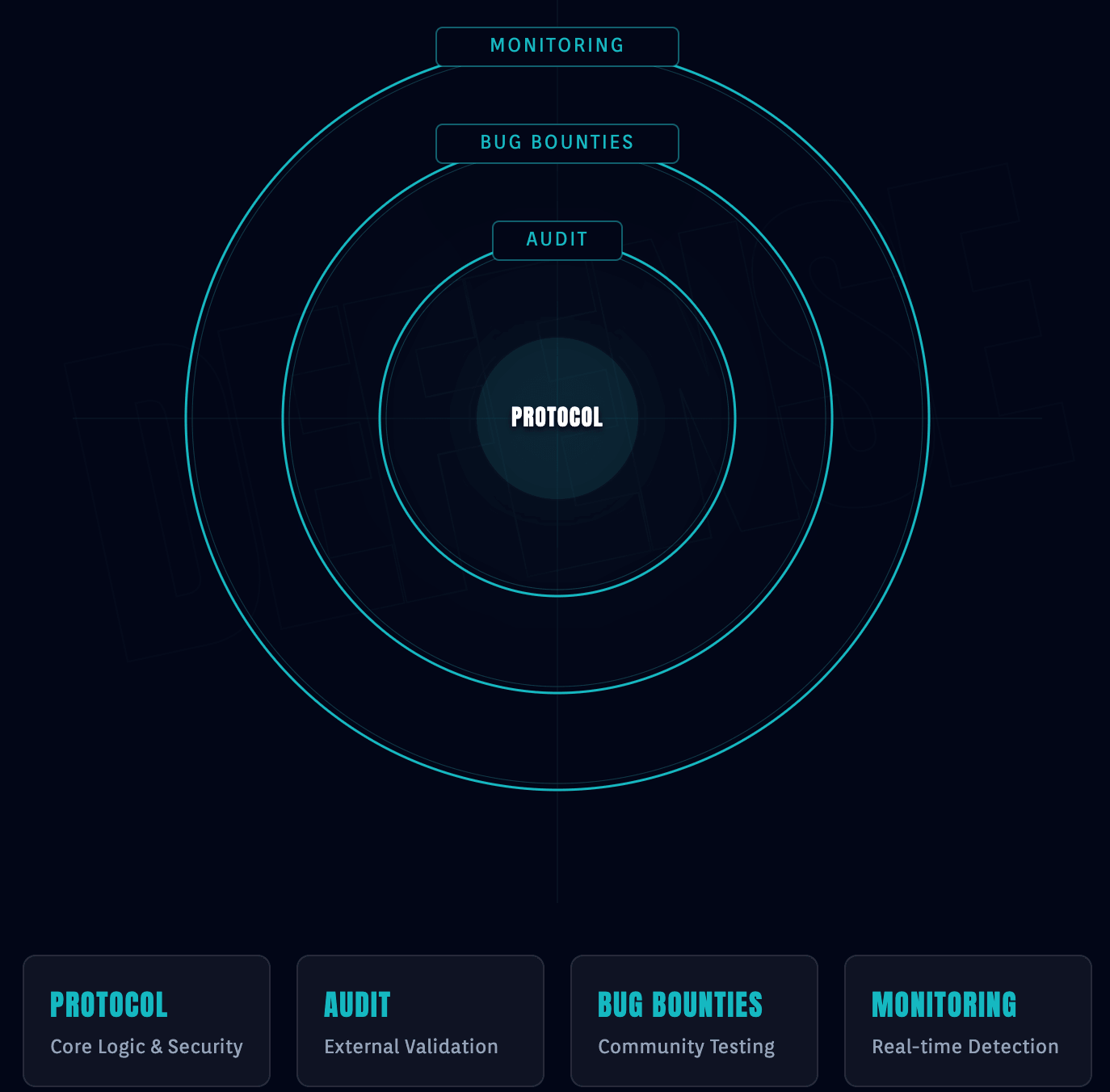
The Full Security Stack (Defense in Depth)
By 2025, a single PDF is no longer enough. Sophisticated allocators look for a holistic security stack that protects the protocol post-deployment:
- Active Bug Bounties: An active program on platforms like Immunefi. The reward should be proportional to your Total Value Locked (TVL).
- Real-time Monitoring: Use of tools like Forta or Hypernative to detect and respond to anomalous transactions in real-time. This is crucial for post-investment monitoring.
- On-chain Circuit Breakers: The ability to pause the protocol automatically if a "black swan" event occurs.
- Protocol Insurance: Coverage from providers like Nexus Mutual or Sherlock. If a third-party underwriter is willing to put capital against your security, it is a massive validation.

Security as a Valuation Multiplier
Founders often view audits as a "security tax." Investors view them as a "valuation multiplier."
A protocol with a rigorous, transparent audit history commands a higher valuation because it reduces the discount rate associated with existential risk. While the upfront smart contract audit cost might seem high during a bridge or Series A round, it is the only way to unlock Tier-1 exchange listings and attract institutional liquidity (whales) who refuse to deposit into unaudited contracts.
The Bottom Line: You aren't just auditing your code to find bugs; you are auditing your code to build the trust necessary to scale.
Next Step for Technical Founders:
Before your next pitch, perform an "internal audit" of your documentation. If your audit reports aren't publicly accessible, or if your "Fixed" status isn't linked to a verified commit hash, fix that first. Transparency is the only currency that matters in Web3 due diligence.
Partner with Zealynx
At Zealynx, we understand that an audit is a critical asset in your fundraising deck. We help you prepare for Technical Due Diligence and eliminate the "code smells" that scare off investors. Our audits are designed to be rigorous, transparent proofs of security that you can proudly present to Tier-1 allocators.
FAQ: Audits & Investor Relations
1. Do investors care about which firm performed the audit?
Yes. Sophisticated investors (especially in Series A+) view the auditor's brand as a proxy for quality. A "Tier 1" audit acts as a strong signal of reliability, while unknown or "budget" auditors may raise questions about your commitment to security and rigorous engineering.
2. Is one audit enough for a mainnet launch?
For unexpected "black swan" events, one audit is rarely sufficient. Investors prefer a "Defense in Depth" strategy that includes multiple independent reviews, active bug bounties on platforms like Immunefi, and real-time monitoring solutions.
3. What is the impact of "Acknowledged" findings in an audit report?
Unfixed "High" or "Critical" issues marked as "Acknowledged" are red flags in TechDD. They imply a tolerance for risk that most institutional investors find unacceptable. Unless there is a documented, unavoidable reason (e.g., specific centralization required for MVP), these should be resolved.
4. How should I present my audit history to investors?
Transparency is key. Maintain a clean, accessible security folder in your data room. Ensure "Fixed" statuses link to verified commit hashes. Presenting a timeline of audits that matches your development lifecycle (rather than a single last-minute check) demonstrates operational maturity.
5. What is Technical Due Diligence (TechDD) for Web3 startups?
Technical Due Diligence (TechDD) is the process where investors evaluate your protocol's code quality, security posture, and engineering practices before investment. Unlike traditional software DD, Web3 TechDD focuses heavily on smart contract security because bugs can result in total capital loss. Investors examine your audit reports, test coverage, bug bounty programs, access controls, and code architecture to assess technical risk and team competency.
6. What is a multi-sig wallet and why do investors require it?
A multi-signature (multi-sig) wallet requires multiple private keys to authorize critical protocol operations like upgrades, minting, or pausing contracts. For example, a 3-of-5 multi-sig means 3 out of 5 designated signers must approve a transaction. Investors require multi-sigs (instead of single EOA control) to prevent rug pulls, reduce insider threat risk, and ensure no single person can compromise the protocol. Combined with a Timelock, it gives users notice before major changes and prevents instant malicious upgrades.
Glossary
| Term | Definition |
|---|---|
| Technical Due Diligence | Investor evaluation process examining smart contract code quality, security posture, and engineering practices before funding. |
| Bug Bounty | Reward program incentivizing security researchers to find and report vulnerabilities before malicious exploitation. |
| Timelock | Smart contract mechanism enforcing mandatory delay between initiating and executing critical protocol changes for transparency. |
| Reentrancy Guard | Smart contract security pattern preventing attackers from recursively calling functions to drain funds during execution. |
| Defense in Depth | Layered security strategy combining multiple independent protections rather than relying on single security measures. |