Back to Blog 

AuditWeb3 Security
Smart Contract Audits vs DeFi Insurance: Which Do You Need in 2026?
By the start of 2026, the "Code is Law" narrative has reached a point of exhaustion. Despite the widespread adoption of formal verification, advanced fuzzing, and multiple audit cycles, the volume of stolen funds has only accelerated. In 2025 alone, losses exceeded $2.17 billion—not because of broken cryptography, but because of a fundamental failure of scope.
For the protocol architect, the lesson of the last year is clear: the traditional "Audit-Deploy-Pray" lifecycle is a legacy methodology. An audit is a point-in-time snapshot of logic; it cannot predict the chaotic interplay of external oracles, liquidity shifts, and upgrading dependencies in a live, adversarial environment.
To survive the current threat landscape, we have to stop viewing audits and insurance as interchangeable substitutes. They are orthogonal components of a necessary defense-in-depth architecture.
The engineering limits of static verification
If audits are failing to prevent billion-dollar hacks, we must examine the computational boundaries of our tools. Even the most sophisticated security firms face theoretical limits in three specific areas.
1. The state explosion problem

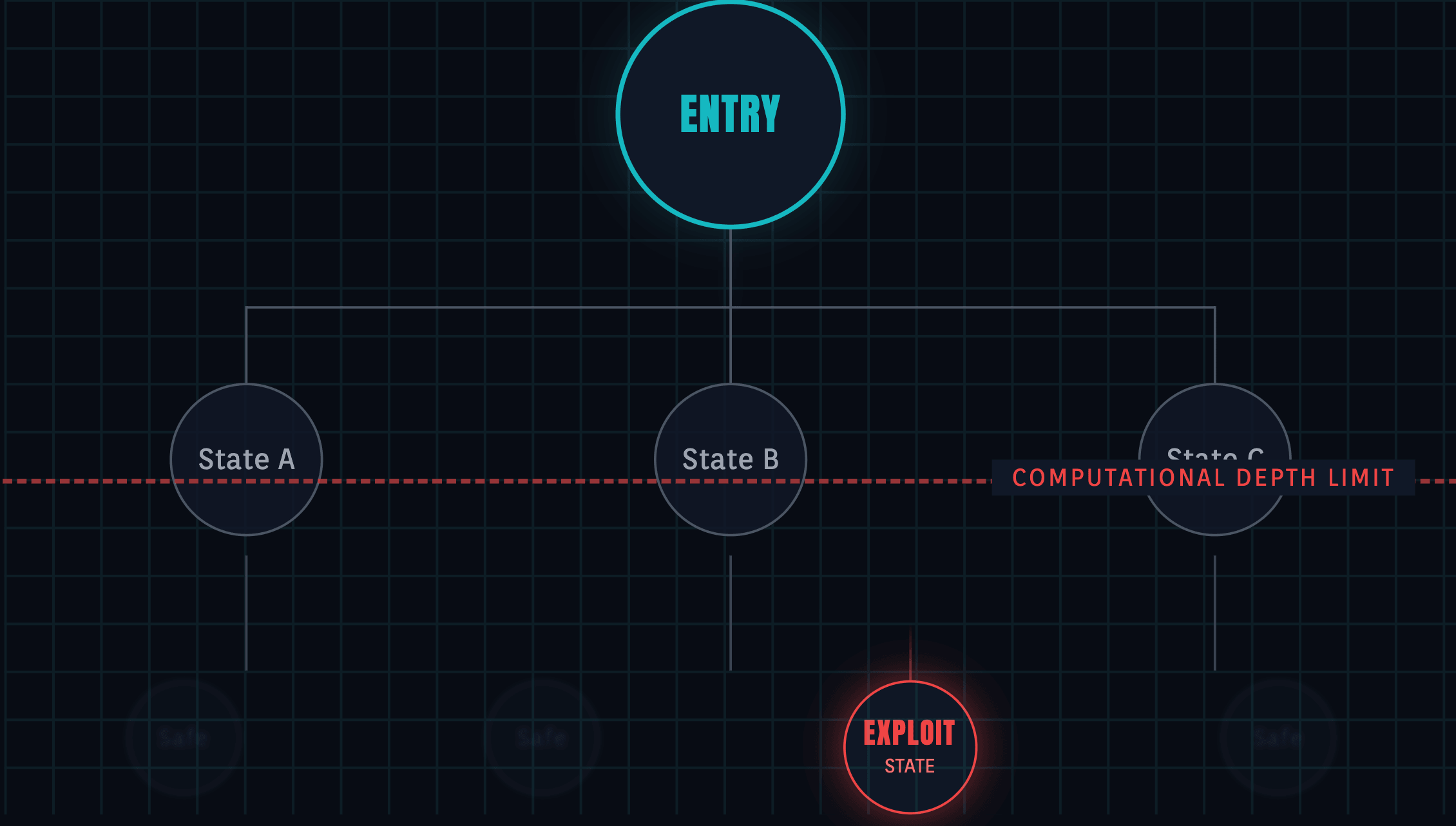
Symbolic execution tools (like Manticore or Mythril) attempt to explore program paths by treating inputs as symbolic variables. However, smart contracts—especially those interacting with composable DeFi primitives—operate in a state space that grows exponentially.
To maintain feasibility, these tools inevitably use heuristics to prune paths or limit loop depths. If a vulnerability exists at an execution depth of , and your tool stopped at , the bug remains invisible. Furthermore, these engines often "mock" external calls. They verify internal consistency but cannot predict systemic instability caused by external state manipulation, such as a flash-loan-induced oracle deviation.
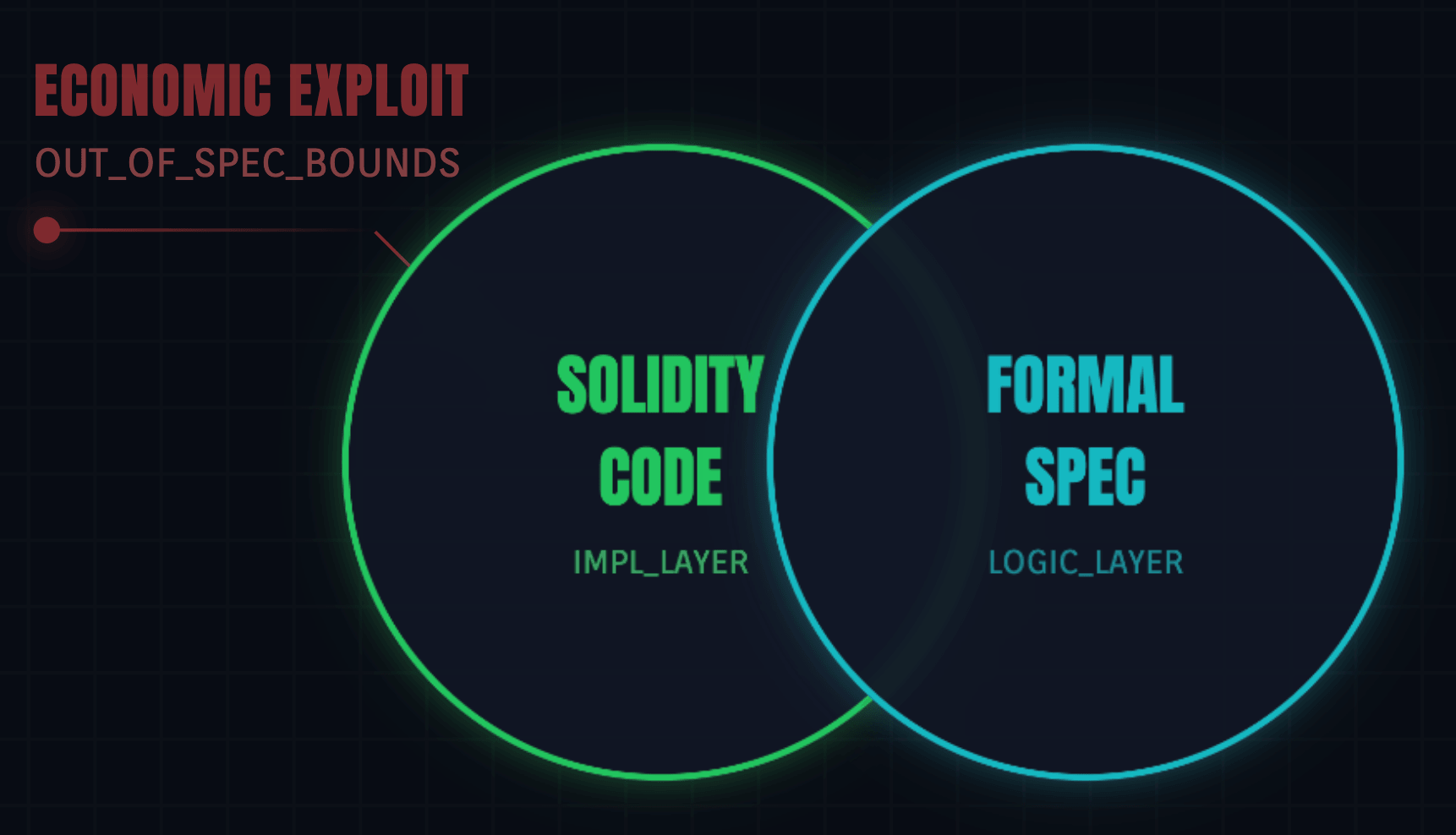
2. The specification gap

Formal Verification (FV) is often called the "gold standard," but it is only as good as its specification. FV can prove that a
withdraw() function only works if balance > amount. It cannot prove that the mathematical formula for calculating amount is economically sound under extreme market conditions.The Balancer V2 exploit of late 2025 is a case study in this "Specification Gap." The protocol had undergone 11 separate audits. The code did exactly what the math allowed, but the math allowed for precision rounding errors that an attacker used to manipulate invariants. The failure wasn't in the code's deviation from the spec, but in the spec's deviation from economic reality.
3. The upgradeability paradox
In 2026, most protocols use proxy patterns for iteration. This introduces the risk of storage collisions—where an upgrade inserts a variable in a way that overwrites critical state in the proxy contract. While tools exist to detect these, complex inheritance structures often create blind spots. More importantly, an audit of Version 1.0 is rendered moot the moment Version 1.1 is deployed. You can audit the code, but you cannot easily audit the governance process that controls the keys.
The industrialization of exploits
The adversary has evolved. We are no longer defending against individual "script kiddies." We are defending against machine-speed, industrialized cyber-warfare.
- AI-driven exploitation: Autonomous agents now reason about novel vulnerabilities, such as identifying specific conditions where integer division favors the attacker. The "time-to-exploit" for a newly deployed vulnerability has collapsed to near zero.
- State-sponsored persistence: Groups like the DPRK now account for a majority of stolen funds, utilizing hybrid attacks that combine on-chain logic exploits with off-chain social engineering (e.g., the "fake job interview" phish).
- Legacy contract risk: Attackers are increasingly targeting deprecated V1 contracts that remain on-chain and share permissions or state with V2, a vector typically outside the scope of a current-version audit.
Insurance as programmatic exception handling
In traditional software engineering, we use
try-catch blocks to handle unexpected runtime errors. Smart contracts lack this; a logic exploit simply succeeds, and the state is permanently altered.In 2026, decentralized insurance functions as the "catch block" for the EVM. It handles the
EconomicInvariantBroken error that the Solidity compiler cannot detect.Parametric architectures (The deterministic firewall)
Parametric insurance is the most "engineer-friendly" model. It relies on hard-coded oracle triggers (e.g., a stablecoin depeg or a validator slashing event). Payouts are atomic and guaranteed by code, removing human subjectivity and claims adjusters from the loop.
Optimistic adjudication (The "fuzzy logic" layer)
For complex math errors or logic exploits that cannot be caught by a price feed, protocols like Sherlock use an Optimistic Oracle mechanism. This crowdsources the "audit" to the post-exploit phase, using economic game theory to adjudicate whether a hack occurred and trigger a payout.
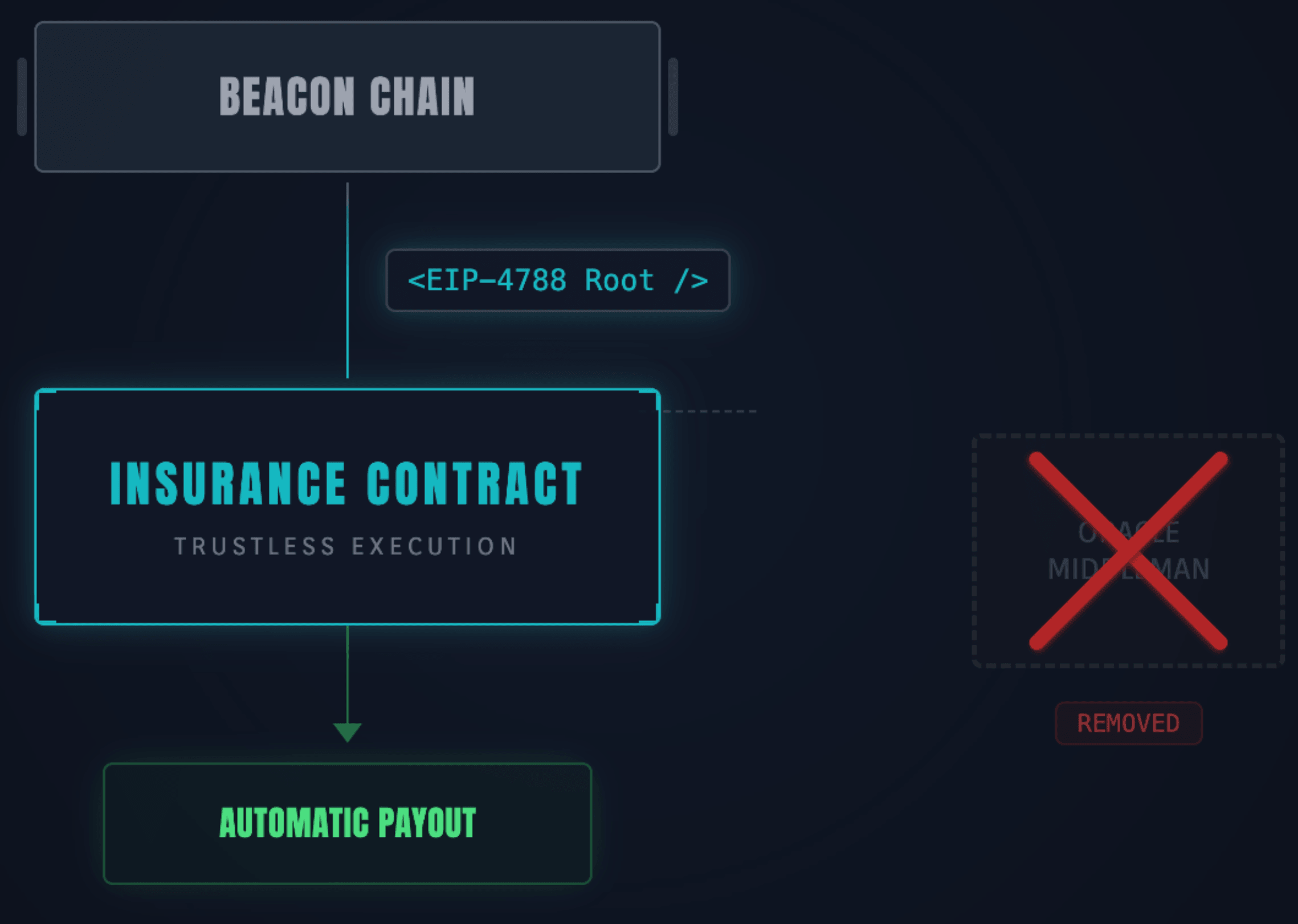
The "native" insurance layer: EIP-4788 and EigenLayer

Insurance is moving closer to the consensus layer. With EIP-4788 making the beacon chain block root available inside the EVM, we can now build trustless slashing insurance.
- Trustless proofs: An insurance contract can verify a Merkle proof against the
BEACON_ROOTSprecompile to confirm a validator's status. If a validator is slashed, the insurance contract automatically pays out without requiring a middleman oracle. - Restaking risks: EigenLayer's "Redistributable Slashing" allows funds to be moved from a malicious operator to the victims. However, since Native ETH cannot yet be redistributed (only burned), third-party insurance remains a prerequisite for protocols using native ETH in restaking strategies.
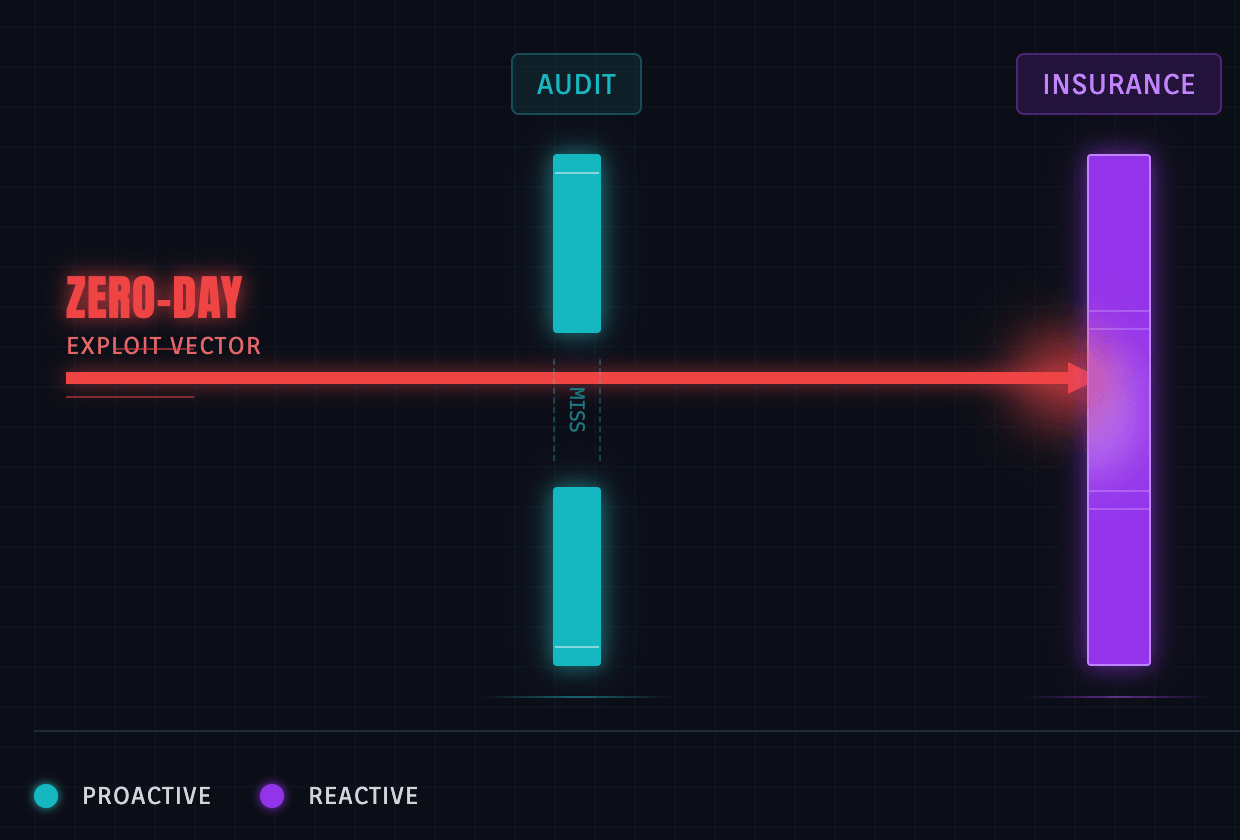
Operationalizing the "Swiss cheese" model
Think of security as the "Swiss Cheese" model: audits are one slice (stopping known bugs), and insurance is the next slice (catching what slips through).

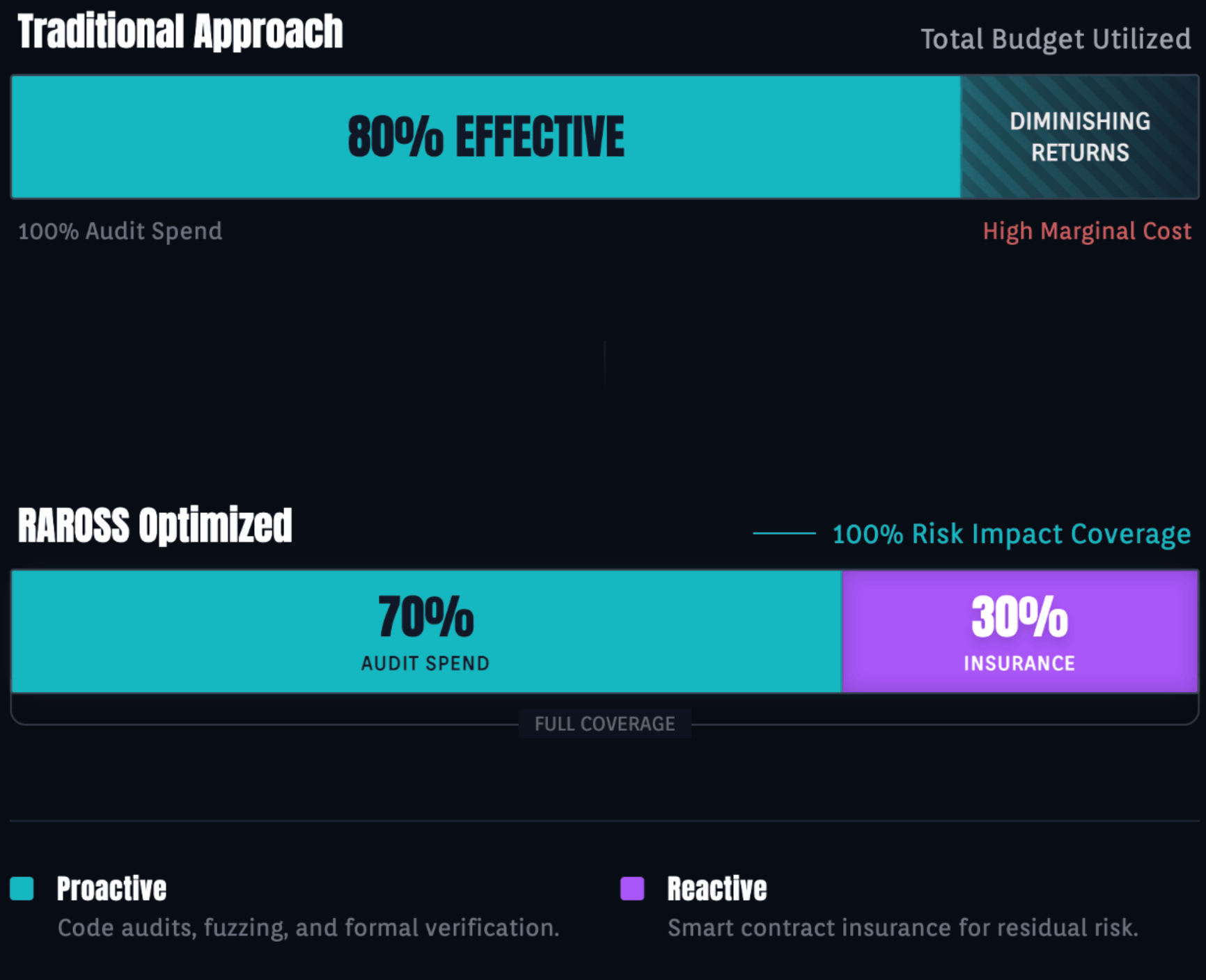
1. Optimization of security spend (RAROSS)

Audits obey the law of diminishing returns. Spending $200k on a third audit to catch the final 1% of bugs is often mathematically sub-optimal. Understanding the true smart contract audit price helps in allocating 70% of the security budget to audits and 30% to insurance premiums that cover the 100% impact of that missing 1%.
2. Design for insurability
Architecture your contracts to expose the state variables required for parametric triggers. If your protocol's solvency depends on a specific invariant, make that invariant queryable by an external insurance oracle.
3. Demand "skin in the game"
The gold standard for 2026 is the audit-backed coverage model. Prioritize security firms that couple their reviews with capital. If an auditor is unwilling to underwrite the risk of their own oversight, their report is merely a suggestion, not a guarantee.
Summary: The engineering mandate
In 2026, the debate is no longer "Audit vs. Insurance." It is a category error, like asking "Brakes vs. Airbags."
- Audits (Brakes): Essential active safety to prevent the crash.
- Insurance (Airbags): Essential passive safety to survive the crash when the brakes fail.
The data proves that the brakes will eventually fail—whether via a rounding error, a compromised admin key, or an AI-generated zero-day. A protocol that is only audited is reckless. A protocol that is insured but not audited is negligent. Only the protocol that integrates both is engineered to survive.
Recommended reading
- Smart contract audit cost in 2026: Pricing benchmarks and guide
- The Power of Fuzzing and Formal Verification in Blockchain Security
- Why Smart Contract Audits Attract Institutional Investors
- Pre-Audit Checklist: How to Prepare for a Smart Contract Audit
- 2025 Exploit Lessons: Retrospective Analysis
Partner with Zealynx
At Zealynx, we understand that security is not a checkbox—it's an economic mandate. We help protocols move beyond basic compliance to build defense-in-depth architectures that attract institutional capital. Whether you need deep invariant analysis, economic modeling, or preparation for insurance underwriting, our team bridges the gap between code and solvency.
FAQ: Smart contract audits & insurance
1. Can insurance replace a smart contract audit?
No. Insurance and audits serve different functions. An audit is a preventative measure ("active safety") designed to catch bugs before deployment. Insurance is a reactive measure ("passive safety") designed to compensate users if a bug is exploited. Relying solely on insurance is prohibitively expensive because premiums for unaudited protocols are often 10-50x higher than for audited ones.
2. Why do audited protocols still get hacked?
Audits are "point-in-time" assessments of code logic, not guarantees of future security. Protocols get hacked due to: 1) Economic exploits (market manipulation that technically follows code rules), 2) Compromised private keys (operational security failures), 3) Upgrades (introducing new bugs into old code), and 4) Dependency failures (an external oracle or token acting unexpectedly).
3. What is the "State Explosion" problem in auditing?
The State Explosion problem refers to the exponential number of possible states a smart contract can be in. Symbolic execution tools try to test every possible path, but as contract complexity grows (especially with external DeFi interactions), the number of paths becomes infinite. Tools must "prune" or ignore some paths to finish running, which means bugs hiding in those deep, untested paths remain undiscovered.
4. How does parametric insurance work for smart contracts?
Parametric insurance pays out automatically based on hard-coded data triggers, without a human claims adjuster. For example, if an on-chain oracle reports that a stablecoin has traded below $0.95 for 6 hours, the smart contract automatically releases payout funds to policyholders. This removes the "claims friction" and ensures immediate liquidity after an event.
5. Is it better to spend budget on a third audit or insurance?
According to the Law of Diminishing Returns, a third audit often provides marginal value (finding minor gas issues) compared to the cost. Allocating that portion of the budget to insurance coverage often provides better "Risk-Adjusted Return on Security Spending" (RAROSS) because it covers 100% of the financial loss from the bugs that even a third audit might miss.
6. What is EIP-4788 and why does it matter for insurance?
EIP-4788 exposes the Ethereum Beacon Chain's block root inside the EVM. This allows smart contracts to trustlessly verify the state of validators. For insurance, this is revolutionary because it enables "trustless slashing insurance"—a contract can mathematically prove a validator was slashed and pay out automatically, without relying on a third-party oracle to report the event.
Glossary
| Term | Definition |
|---|---|
| State Explosion Problem | The exponential growth of possible execution paths in smart contracts that makes exhaustive symbolic verification computationally infeasible. |
| Specification Gap | The disconnect between what formal verification can prove about code logic and the economic soundness of that logic under real-world conditions. |
| Parametric Insurance | A DeFi insurance model that uses hard-coded oracle triggers to execute automatic payouts without human claims adjusters. |
| EIP-4788 | An Ethereum protocol upgrade that exposes the beacon chain block root inside the EVM, enabling trustless validator state verification. |
| RAROSS | Risk-Adjusted Return on Security Spending—a framework for optimizing the allocation between audit costs and insurance premiums. |
| Optimistic Adjudication | A post-exploit mechanism that crowdsources hack verification using economic game theory to trigger insurance payouts. |